How to identify and protect against routing attacks in the Lightning Network
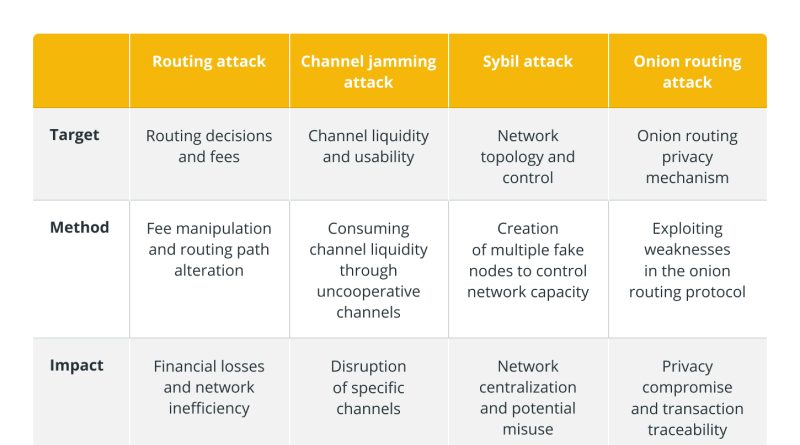
In the Lightning Network, routing attacks refer to ponder attempts by users to take advantage of weak points in the routing system for individual gain.A common routing attack, for instance, entails an individual actively imposing high routing charges, making it expensive for other users to path their payments through that participants channels. Additionally, they may try to divert payments sent out to licensed receivers to their own channels.To minimize the dangers brought on by routing assaults, Lightning Network designers and users must be constantly careful, upgrading network security, establishing routing algorithms and motivating accountable node operation.Common routing attacks in the Lightning NetworkRouting charge snipingIn this attack, a rogue node might purposefully establish excessive routing fees for a payment channel it controls. Routing attacks can take lots of types, however they normally intend to stop the network from working correctly or unjustly earnings from routing fees.These attacks sometimes take the form of unusual payment failures, unanticipated routing fees, and abrupt modifications in channel liquidity. A routing attack is a wider term that refers to a number of malicious techniques used to manipulate payment routing for benefit or to interfere with networks.These methods might require purposefully rejecting payments, charging extreme routing costs or creating inefficient paths. On the other hand, channel jamming is a particular kind of routing attack in which a malicious node floods a specific channel with a number of small, not successful payments, lessening the channels liquidity and making it difficult for trusted users to path payments through it.While channel jamming is one method to interfere with routing, routing attacks go beyond that and consist of a range of strategies to endanger the security of the network.
In the Lightning Network, routing attacks refer to ponder attempts by users to take benefit of weaknesses in the routing system for individual gain.A normal routing attack, for circumstances, requires a participant purposefully imposing high routing fees, making it pricey for other users to path their payments through that participants channels. Furthermore, they may try to divert payments sent to authorized receivers to their own channels.To lower the risks brought on by routing assaults, Lightning Network users and designers should be continuously careful, updating network security, establishing routing algorithms and motivating responsible node operation.Common routing attacks in the Lightning NetworkRouting cost snipingIn this attack, a rogue node might purposefully develop excessive routing costs for a payment channel it manages. On the other hand, channel jamming is a specific kind of routing attack in which a harmful node floods a particular channel with several small, unsuccessful payments, decreasing the channels liquidity and making it impossible for trustworthy users to route payments through it.While channel jamming is one method to interfere with routing, routing attacks go beyond that and consist of a range of tactics to endanger the security of the network.