What are address poisoning attacks in crypto and how to avoid them?
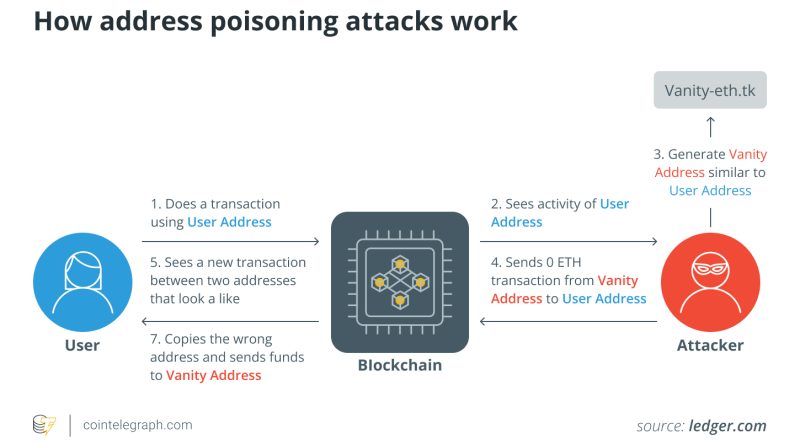
Address poisoning attacks are harmful techniques used by attackers who can reroute traffic, disrupt services, or acquire unapproved access to delicate data by placing bogus data or changing routing tables. The integrity of data and network security are seriously threatened by these attacks, which take advantage of flaws in network protocols.This short article will describe what address poisoning attacks are, their repercussions and types, and how to safeguard oneself against such attacks.Address poisoning attacks in crypto, explainedIn the world of cryptocurrencies, hostile actions where assaulters affect or deceive customers by damaging cryptocurrency addresses are described as address poisoning attacks.On a blockchain network, these addresses, which are comprised of distinct alphanumeric strings, function as the source or destination of deals. These attacks use a variety of techniques to undermine the stability and security of cryptographic wallets and transactions.Address poisoning attacks in the crypto area are primarily utilized to either unlawfully obtain digital properties or hinder the smooth operation of blockchain networks. These attacks may encompass: TheftAttackers might trick users into transmitting their funds to harmful addresses using strategies such as phishing, deal interception or address manipulation.DisruptionAddress poisoning can be used to interfere with the regular operations of blockchain networks by introducing congestion, hold-ups or interruptions in deals and clever agreements, lowering the efficiency of the network.DeceptionAttackers often try to misinform cryptocurrency users by impersonating popular figures. This undermines community trust in the network and may lead to erroneous deals or confusion among users.To safeguard digital properties and the basic integrity of blockchain technology, address poisoning attacks highlight the significance of stringent security treatments and consistent attention within the cryptocurrency ecosystem.Related: How to mitigate the security risks associated with crypto paymentsTypes of address poisoning attacksAddress poisoning attacks in crypto consist of phishing, transaction interception, address reuse exploitation, Sybil attacks, fake QR codes, address spoofing and clever contract vulnerabilities, each posing unique threats to users possessions and network integrity.Phishing attacksIn the cryptocurrency world, phishing attacks are a common kind of address poisoning, which includes criminal actors developing phony sites, e-mails or communications that closely resemble trusted business like cryptocurrency exchanges or wallet providers.These deceitful platforms try to trick unsuspecting users into revealing their login details, private secrets or mnemonic expressions (recovery/seed phrases). When acquired, attackers can perform unlawful deals and get unauthorized access to victims Bitcoin (BTC) possessions, for example.For circumstances, hackers may construct a fake exchange site that looks exactly like the real thing and ask customers to log in. Once they do so, the assailants can get access to customer funds on the real exchange, which would result in significant monetary losses.Transaction interceptionAnother approach of address poisoning is transaction interception, in which aggressors obstruct legitimate cryptocurrency transactions and alter the location address. Funds predestined for the genuine receiver are diverted by altering the recipient address to one under the assaulters control. This type of attack regularly includes malware compromising a users device or network or both.Address recycle exploitationAttackers monitor the blockchain for circumstances of address repeating prior to utilizing such events to their advantage. Because it might expose the addresss transaction history and vulnerabilities, reusing addresses can be risky for security. These weak points are utilized by destructive actors to gain access to user wallets and steal funds.For instance, if a user consistently gets funds from the same Ethereum address, an aggressor might see this pattern and take advantage of a defect in the users wallet software application to access the users funds without authorization.Sybil attacksTo put in out of proportion control over a cryptocurrency networks performance, Sybil attacks entail the production of a number of false identities or nodes. With this control, assailants are able to modify data, trick users, and possibly threaten the security of the network.Attackers might use a great deal of deceitful nodes in the context of proof-of-stake (PoS) blockchain networks to considerably impact the consensus system, providing them the ability to customize deals and possibly double-spend cryptocurrencies.Fake QR codes or payment addressesAddress poisoning can also take place when phony payment addresses or QR codes are dispersed. Aggressors often deliver these bogus codes in physical type to unwary users in an effort to deceive them into sending out cryptocurrency to a location they did not plan.For example, a hacker may share QR codes for cryptocurrency wallets that look real but in fact consist of small changes to the encoded address. Users who scan these codes unintentionally send cash to the attackers address rather than that of the intended receiver, which causes financial losses.Address spoofingAttackers who utilize address spoofing produce cryptocurrency addresses that closely look like real ones. The idea is to fool users into moving cash to the assaulters address rather than the one belonging to the desired recipient. The visual resemblance in between the phony address and the genuine one is utilized in this method of address poisoning.An aggressor might, for example, create a Bitcoin address that carefully imitates the contribution address of a credible charity. Uninformed donors might accidentally transfer money to the aggressors address while sending contributions to the company, diverting the funds from their intended use.Smart contract vulnerabilitiesAttackers benefit from defects or vulnerabilities in decentralized applications (DApps) or clever contracts on blockchain systems to bring out address poisoning. Attackers can reroute money or cause the agreement to behave unintentionally by adjusting how deals are performed. Users may suffer cash losses as a result, and decentralized financing (DeFi) services may experience disruptions.Consequences of address poisoning attacksAddress poisoning attacks can have terrible impacts on both individual users and the stability of blockchain networks. Due to the fact that aggressors might steal crypto holdings or alter transactions to reroute cash to their own wallets, these assaults frequently cause large financial losses for their victims.Beyond monetary losses, these attacks may likewise lead to a decrease in confidence among cryptocurrency users. Users rely on the security and dependability of blockchain networks and related services may be harmed if they fall for deceptive plans or have their valuables stolen.Additionally, some address poisoning assaults, such as Sybil attacks or the abuse of wise agreement defects, can avoid blockchain networks from operating normally, resulting in delays, congestion or unanticipated consequences that have an impact on the entire community. These effects highlight the requirement for strong security controls and user awareness in the crypto ecosystem to decrease the risks of address poisoning attacks.Related: How to put words into a Bitcoin address? Heres how vanity addresses workHow to prevent address poisoning attacksTo safeguard users digital assets and keep blockchain networks protected, it is essential to prevent address poisoning attacks in the cryptocurrency world. The following methods might help prevent being a target of such attacks: Use fresh addressesBy producing a fresh crypto wallet address for each transaction, the possibility of aggressors connecting an address to a persons identity or past transactions can be decreased. Address poisoning attacks can be decreased by utilizing hierarchical deterministic (HD) wallets, which develop brand-new addresses for each transaction and lessen the predictability of addresses. Utilizing an HD wallet increases a users protection versus address poisoning attacks due to the fact that the wallets automatic address rotation makes it harder for hackers to reroute funds.Utilize hardware walletsWhen compared to software application wallets, hardware wallets are a more protected option. They minimize exposure by keeping private keys offline.Exercise care when revealing public addressesPeople must work out caution when revealing their crypto addresses in the general public sphere, specifically on social networks websites, and should decide for utilizing pseudonyms.Choose respectable walletsIt is necessary to use widely known wallet suppliers that are known for their security functions and routine software application updates to safeguard oneself from address poisoning and other attacks.Regular updatesTo stay protected against address poisoning attacks, it is necessary to update the wallet software regularly with the latest security fixes.Implement whitelistingUse whitelisting to limit deals to reputable sources. Some wallets or services permit users to whitelist particular addresses that can send funds to their wallets.Consider multisig walletsWallets that need numerous private secrets to authorize a transaction are called multisignature (multisig) wallets. These wallets can offer an additional degree of security by needing several signatures to authorize a transaction.Utilize blockchain analysis toolsTo area potentially hazardous conduct, individuals can track and examine inbound deals utilizing blockchain analysis tools. Sending seemingly unimportant, little quantities of crypto (dust) to many addresses is a typical practice called dusting. Experts can find possible poisoning efforts by analyzing these dust trade patterns.Unspent deal outputs (UTXOs) with small amounts of cryptocurrency are frequently the effect of dust deals. Analysts can find possibly poisoned addresses by locating UTXOs connected to dust transactions.Report believed attacksIndividuals should react immediately in case of a suspected address poisoning attack by contacting the business that provides their crypto wallet through the main support channels and detailing the occurrence.Additionally, they can report the event to the appropriate police or regulative authorities for further examination and possible legal action if the attack included significant financial harm or malevolent intent. To decrease possible threats and protect both specific and group interests in the cryptocurrency environment, timely reporting is important.
Users who scan these codes inadvertently send out cash to the assaulters address rather than that of the desired receiver, which causes monetary losses.Address spoofingAttackers who utilize address spoofing produce cryptocurrency addresses that closely resemble real ones. The visual similarity in between the fake address and the real one is used in this method of address poisoning.An attacker might, for instance, produce a Bitcoin address that closely imitates the contribution address of a trusted charity. Unaware donors might accidentally transfer cash to the opponents address while sending donations to the organization, diverting the funds from their intended use.Smart contract vulnerabilitiesAttackers take advantage of flaws or vulnerabilities in decentralized applications (DApps) or clever agreements on blockchain systems to bring out address poisoning. Heres how vanity addresses workHow to avoid address poisoning attacksTo secure users digital properties and keep blockchain networks protected, it is important to avoid address poisoning assaults in the cryptocurrency world. Address poisoning attacks can be reduced by utilizing hierarchical deterministic (HD) wallets, which produce brand-new addresses for each transaction and lessen the predictability of addresses.
Related Content
- Crypto VC: Risk and investment strategies with Shima Capital
- What El Salvador’s Bitcoin Law Has Brought To The Country
- Hodling hard: Bitcoin’s long-term investors own over 76% of all BTC for the first time
- Bitcoin Price And Risk Assets Jump In Correlated Move
- NFT art pioneer wants to upload her brain so she can live forever: Josie Bellini, NFT Creator