Exclusive: Hackers selling discounted tokens linked to CoinEx, Stake hacks
Blockchain analytics private investigators have actually discovered a private linked to a cryptocurrency laundering operation that is using stolen tokens at discounted costs from current high-profile exchange hacks.Speaking exclusively to Cointelegraph, an agent from blockchain security firm Match Systems described how examinations into a number of major breaches featuring similar techniques through the summer months of 2023 have actually pointed to a person who is apparently offering taken cryptocurrency tokens by means of peer-to-peer transfers.Related: CoinEx hack: Compromised private keys led to $70M theftThe private investigators managed to make and identify contact with a specific on Telegram offering taken possessions. The group confirmed that the user was in control of an address containing over $6 million worth of cryptocurrencies after receiving a little transaction from the matching address.A message from the seller marketing taken tokens being connected to CoinEx and Stake hacks. Following initial conversations, the owner of the address reported that the preliminary assets on deal had actually been offered and that brand-new tokens would be offered some 3 weeks later on:” Maintaining our contact, this specific informed us about the commencement of brand-new asset sales.
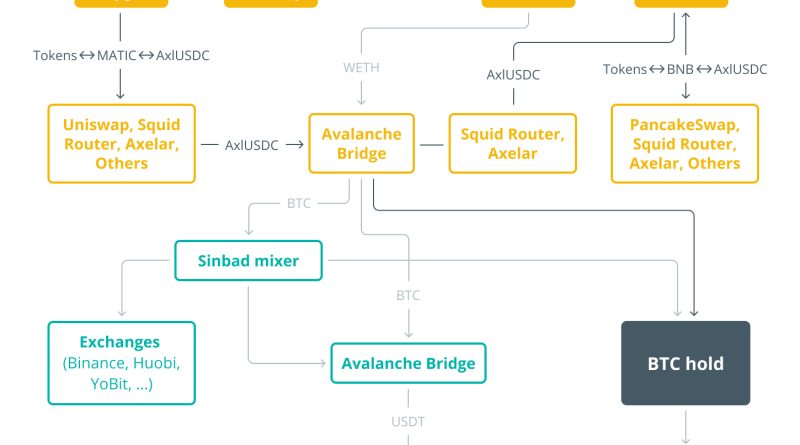
Blockchain analytics private investigators have actually revealed an individual connected to a cryptocurrency laundering operation that is offering stolen tokens at reduced prices from recent high-profile exchange hacks.Speaking exclusively to Cointelegraph, a representative from blockchain security company Match Systems detailed how investigations into a number of major breaches including comparable techniques through the summertime of 2023 have pointed to an individual who is allegedly selling stolen cryptocurrency tokens through peer-to-peer transfers.Related: CoinEx hack: Compromised personal secrets resulted in $70M theftThe investigators managed to make and identify contact with a specific on Telegram offering taken assets. The group validated that the user was in control of an address containing over $6 million worth of cryptocurrencies after getting a small transaction from the corresponding address.A message from the seller marketing stolen tokens being connected to CoinEx and Stake hacks. Source: Match SystemsThe exchange of stolen properties was then performed through a specially created Telegram bot, which provided a 3% discount rate off the tokens market cost. Following initial conversations, the owner of the address reported that the preliminary assets available had been offered and that new tokens would be available some 3 weeks later:” Maintaining our contact, this private alerted us about the beginning of new possession sales. Based upon the offered information, it is sensible to assume that these are funds from CoinEx or Stake business.” The Match Systems team has actually not had the ability to totally identify the individual but has actually narrowed down their area to the European time zone based upon numerous screenshots they had actually gotten and timings of conversations:” We think he is not part of the core group however is related to them, potentially having actually been de-anonymized as an assurance that he will not misuse the delegated properties.” The individual also reportedly showed “unsteady” and “erratic” behavior throughout various interactions, quickly leaving conversations with reasons like “Sorry, I should go; my mom is calling me to dinner”.” Typically, he offers a 3% discount rate. Formerly, when we initially identified him, he would send out 3.14 TRX as a form of evidence to possible clients.” Match Systems informed Cointelegraph that the private accepted Bitcoin (BTC) as a means of payment for the discounted taken tokens and had formerly offered $6 million worth of TRON (TRX) tokens. The most recent offering from the Telegram user has actually noted $50 million worth of TRX, Ether (ETH) and Binance Smart Chain (BSC) tokens.Blockchain security company CertiK formerly detailed the motion of taken funds from the Stake break-in in correspondence with Cointelegraph, with around $4.8 million of the total $41 million being laundered through various token motions and cross-chain swaps.FBI later recognized North Korean Lazarus Group hackers as the offenders of the Stake attack, while cyber security firm SlowMist likewise linked the $55 million CoinEx hack to the North Korean group. This is in slight contrast to info gotten by Cointelegraph from Match Systems which suggests that the criminals of the CoinEx and Stake hacks had somewhat various identifiers in methodology.Their analysis highlights that previous Lazarus Group laundering efforts did not include Commonwealth of Independent States (CIS) countries like Russia and Ukraine while the 2023 summertime hacks saw taken funds being actively laundered in these jurisdictions.Related: Stake hack of $41M was carried out by North Korean group: FBILazarus hackers left very little digital footprints behind while recent occurrences have left lots of breadcrumbs for private investigators. Social engineering has also been identified as a key attack vector in the summer season hacks while Lazarus Group targeted “mathematical vulnerabilities”. The firm notes that Lazarus hackers typically utilized Tornado Cash to wash stolen cryptocurrency while recent incidents have actually seen funds blended through procedures like Sinbad and Wasabi. Key similarities are still considerable. All these hacks have used BTC wallets as the primary repository for taken possessions as well as the Avalanche Bridge and mixers for token laundering.Blockchain data examined at the end of Sept. 2023 recommends that North Korean hackers have actually taken an estimated $47 million worth of cryptocurrency this year, including $42.5 million in BTC and $1.9 million ETH.Magazine: Blockchain investigators: Mt. Gox collapse saw birth of Chainalysis
Related Content
- Deutsche Bank crypto plans aid Bitcoin price trip to $27.5K June highs
- JPMorgan forecasts limited downside for crypto markets: Report
- Why is Solana price up this week?
- ‘XRP is not a security. Period’ — Crypto lawyers on Ripple’s case amid SEC appeal
- Bitcoin price holds steady as S&P 500 plunges to 110-day low