Lazarus used ‘KANDYKORN’ malware in attempt to compromise exchange —Elastic
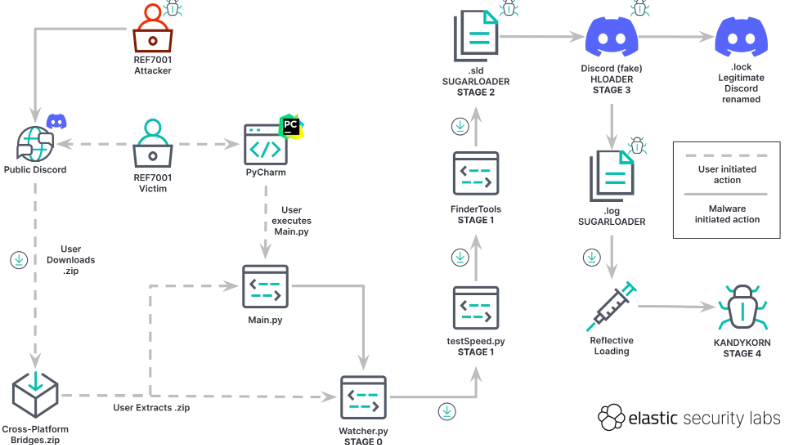
Elastic has actually named the brand-new malware “KANDYKORN” and the loader program that loads it into memory “SUGARLOAD,” as the loader file has an unique “. This file was obfuscated using a “binary packer,” Elastic stated, allowing it to bypass most malware detection programs. According to Elastic, they ran VirusTotal malware detection on SUGARLOADER, and the detector declared that the file was not malicious.Related: Crypto firms are careful: Lazarus brand-new malware can now bypass detectionOnce SUGARLOADER was downloaded into the computer system, it connected to a remote server and downloaded KANDYKORN directly into the devices memory.
Thank you for reading this post, don't forget to subscribe!
Elastic has named the new malware “KANDYKORN” and the loader program that loads it into memory “SUGARLOAD,” as the loader file has a novel “. This file was obfuscated utilizing a “binary packer,” Elastic stated, allowing it to bypass most malware detection programs. According to Elastic, they ran VirusTotal malware detection on SUGARLOADER, and the detector declared that the file was not malicious.Related: Crypto companies beware: Lazarus new malware can now bypass detectionOnce SUGARLOADER was downloaded into the computer system, it connected to a remote server and downloaded KANDYKORN directly into the gadgets memory.
Related Content
- Trezor CEO cites usability as top factor for the hardware wallet: BTC Prague
- Coinbase’s Base launches mainnet for builders, will onboard users in August
- Sotheby’s launches on-chain secondary NFT marketplace: Nifty Newsletter, April 26–May 2
- Unlocking the Secrets of Successful Cryptocurrency Investing: The Power of Compounding Interest and Long-Term Strategies
- Second-biggest US bank failure — 5 things to know in Bitcoin this week