Lazarus used ‘Kandykorn’ malware in attempt to compromise exchange — Elastic
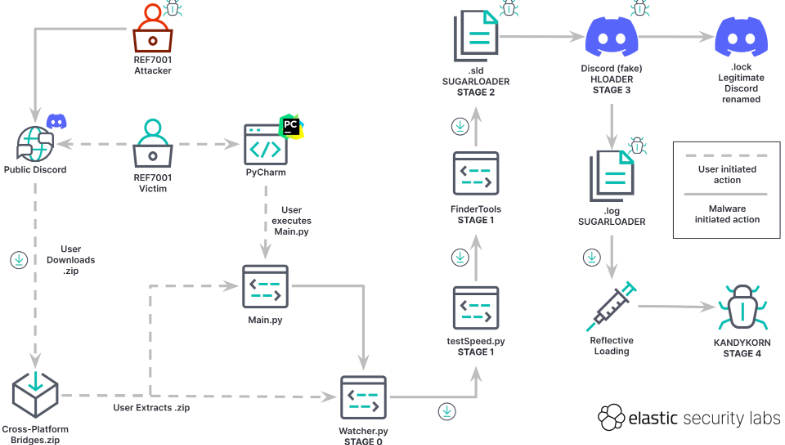
Elastic has actually called the new malware “Kandykorn” and the loader program that loads it into memory “Sugarload,” as the loader file has a novel “. This file was obfuscated utilizing a “binary packer,” Elastic mentioned, enabling it to bypass most malware detection programs. The command “0xD3” can be used to list the contents of a directory on the victims computer, and “resp_file_down” can be used to transfer any of the victims files to the enemys computer.Elastic thinks that the attack occurred in April 2023.
Elastic has actually called the brand-new malware “Kandykorn” and the loader program that loads it into memory “Sugarload,” as the loader file has an unique “. This file was obfuscated utilizing a “binary packer,” Elastic specified, allowing it to bypass most malware detection programs. The command “0xD3” can be used to list the contents of a directory site on the victims computer system, and “resp_file_down” can be used to transfer any of the victims files to the aggressors computer.Elastic believes that the attack happened in April 2023.
Related Content
- Ethereum’s 8th birthday: Crypto industry shares its top moments
- BlockFi’s Chapter 11 plan progresses with conditional court approval
- Decoding Crypto: Understanding Bitcoin, Ethereum, and Beyond
- In 2023, Bitcoin Will Enter The ‘And Then They Fight You’ Stage
- Price analysis 6/14: BTC, ETH, BNB, XRP, ADA, DOGE, SOL, MATIC, LTC, DOT