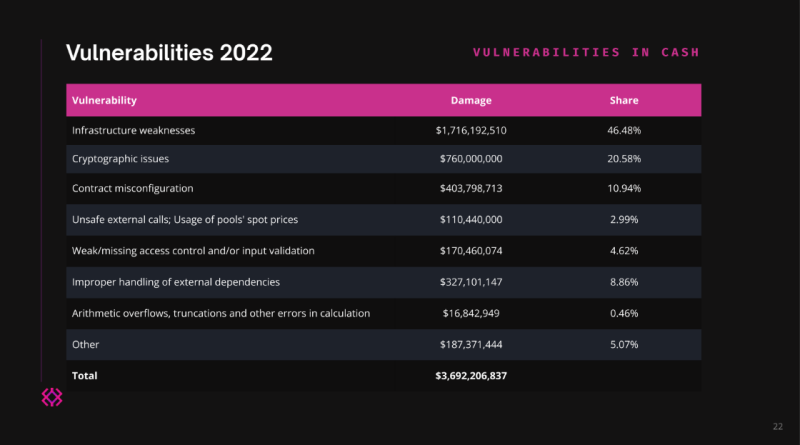
46% of crypto lost from exploits is due to traditional Web2 flaws — Immunefi
A new report from blockchain security platform Immunefi recommends that almost half of all crypto lost from Web3 exploits is because of Web2 security concerns such as dripped private keys. The report, released on Nov. 15, looked back at the history of crypto exploits in 2022, categorizing them into various types of vulnerabilities. It concluded that a complete 46.48% of the crypto lost from exploits in 2022 was not from wise agreement defects but rather from “facilities weaknesses” or issues with the establishing firms computer system systems.Categories of Web3 vulnerabilities. Source: ImmunefiWhen thinking about the variety of incidents rather of the value of crypto lost, Web2 vulnerabilities were a smaller part of the overall at 26.56%, although they were still the second-largest category.Immunefis report left out exit frauds or other frauds, in addition to exploits that happened entirely because of market controls. Due to the fact that of a security vulnerability, it just considered attacks that occurred. Of these, it found that attacks fall under three broad categories. First, some attacks take place because the smart contract consists of a style defect. Immunefi pointed out the BNB Chain bridge hack as an example of this type of vulnerability. Second, some attacks happen because, despite the fact that the wise agreement is developed well, the code executing the design is flawed. Immunefi cited the Qbit hack as an example of this category.Finally, a third category of vulnerability is “infrastructure weaknesses,” which Immunefi defined as “the IT-infrastructure on which a smart agreement operates– for instance virtual machines, personal secrets, etc” As an example of this kind of vulnerability, Immunefi listed the Ronin bridge hack, which was caused by an opponent getting control of five out of 9 Ronin nodes validator signatures.Related: Uniswap DAO debate shows devs still have a hard time to protect cross-chain bridgesImmunefi broke down these categories further into subcategories. When it pertains to infrastructure weak points, these can be brought on by a worker leaking a personal secret (for instance, by sending it across an insecure channel), using a weak passphrase for a crucial vault, problems with tw-factor authentication, DNS hijacking, BGP hijacking, a hot wallet compromise, or using weak encryption methods and storing them in plaintext.While these facilities vulnerabilities triggered the best amount of losses compared to other classifications, the second-largest cause of losses was “cryptographic concerns” such as Merkle tree mistakes, signature replayability and foreseeable random number generation. Cryptographic issues resulted in 20.58% of the total value of losses in 2022. Another typical vulnerability was “weak/missing gain access to control and/or input validation,” the report specified. This kind of flaw led to just 4.62% of the losses in terms of worth, but it was the biggest factor in terms of the variety of occurrences, as 30.47% of all incidents were brought on by it.
Related Content
- How Improving The UI And UX Of Bitcoin Nodes Could Benefit Everyone
- Blockchain arms race risks being won by ‘adversarial nations’ — US crypto lobby group
- Bitcoin price surge sees significant asset outflow on crypto exchanges
- Telegram Wallet bot enables in-app payments in Bitcoin, USDT and TON
- China’s surprise NFT move, Hong Kong’s $15M Bitcoin fund: Asia Express