Level Finance confirms $1M exploit due to buggy smart contract
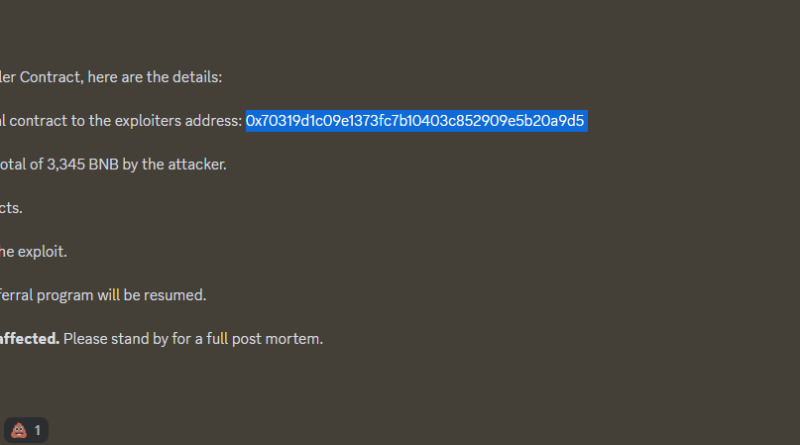
– 214k LVL tokens drained pipes to exploiters address.- Attacker swapped LVL to 3,345 BNB- Exploit was separated from other contracts.– LEVEL Finance #RealYield (@Level__Finance) May 1, 2023
Thank you for reading this post, don't forget to subscribe!
According to blockchain security firm Peckshield, Level Finances “LevelReferralControllerV2” smart agreement consisted of a bug that permitted for “repetitive referral claims” from the exact same date. This was verified by Level Finance in a later statement made on Discord.
Data from Binance chain explorer BSC Scan, the V2 controller agreement reveals multiple calls of the “claim several” function over the past 48 hours.At the time of writing, the application of the contract does not appear to have actually been changed considering that the advent of the attack, nevertheless Level Finance says that it will deploy a new application of the referral contract within the next 12 hours.The exchange also kept in mind that its liquidity swimming pools and related DAOs remain unaffected by the attack. Related: Aprils crypto hacks, rip-offs and exploits lead to $103M lost– CertiKAccording to @DeDotFiSecurity on Twitter, the team states that it has “momentarily shut down the recommendation program,” which has stopped the exploit.
— LEVEL Finance #RealYield (@Level__Finance) May 1, 2023
According to blockchain security firm Peckshield, Level Finances “LevelReferralControllerV2” smart contract included a bug that allowed for “repetitive recommendation claims” from the very same date. Information from Binance chain explorer BSC Scan, the V2 controller contract reveals multiple calls of the “claim multiple” function over the past 48 hours.At the time of writing, the implementation of the contract does not appear to have been altered since the development of the attack, nevertheless Level Finance says that it will release a brand-new application of the recommendation contract within the next 12 hours.The exchange likewise noted that its liquidity swimming pools and associated DAOs remain untouched by the attack.
Related Content
- The Future of Finance: Why You Should Consider Investing in Cryptocurrencies like Bitcoin
- 46% of crypto lost from exploits is due to traditional Web2 flaws — Immunefi
- Spain says masks no longer totally obligatory indoors
- Tencent-backed Everledger collapses amid lack of funding: Report
- Mark Cuban loses $870K in hot wallet hack