Crypto phishing scams: How users can stay protected
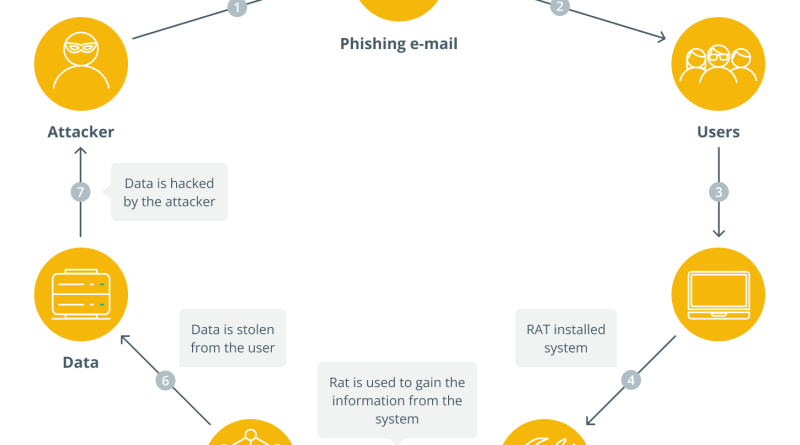
In the ever-evolving and fast-paced world of cryptocurrency, where digital assets are exchanged, and fortunes can be made, a hiding danger threatens the safety of both experienced investors and newbies alike: crypto phishing frauds. These plans are created to make use of the trust and vulnerability of people, intending to fool them into revealing their sensitive details and even parting with their hard-earned crypto holdings.As the appeal of cryptocurrencies continues to increase, so does the elegance of phishing methods used by cybercriminals. From impersonating genuine exchanges and wallets to crafting engaging social engineering tactics, these fraudsters stop at absolutely nothing to get unapproved access to your digital assets.Malicious stars use different approaches of social engineering to target their victims. With social engineering strategies, fraudsters manipulate users feelings and develop a sense of trust and urgency.Eric Parker, CEO and co-founder of Giddy– a noncustodial wallet smart wallet– told Cointelegraph, “Did somebody connect to you without you asking? Thats one of the most significant general rules you can use. Customer support hardly ever, if ever, proactively reaches out to you, so you ought to always be suspicious of messages stating you require to do something about it on your account.””Same idea with free cash: If somebody is messaging you because they want to offer you complimentary cash, its likely, not real. Be careful of any message that feels too great to be real or offers you an immediate sense of urgency or fear to make you act quickly.”Email and messaging scamsOne typical technique used in crypto phishing rip-offs is impersonating relied on entities, such as cryptocurrency exchanges or wallet service providers. The scammers send out emails or messages that appear to be from these legitimate organizations, using comparable branding, logo designs and email addresses. They intend to trick receivers into thinking that the interaction is from a trustworthy source.To attain this, the scammers may utilize methods like email spoofing, where they forge the senders email address to make it appear as if its originating from a genuine company. They may likewise utilize social engineering tactics to individualize the messages and make them seem more genuine. By impersonating relied on entities, scammers exploit the trust and credibility related to these organizations to trick users into acting that jeopardize their security.Fake assistance requestsCrypto phishing scammers frequently impersonate customer assistance representatives of legitimate cryptocurrency exchanges or wallet suppliers. They send messages or e-mails to unwary users, claiming an issue with their account or a pending transaction that needs instant attention. The scammers supply a contact technique or a link to a fake assistance site where users are prompted to enter their login credentials or other delicate information.Omri Lahav, CEO and co-founder of Blockfence– a crypto-security web browser extension– informed Cointelegraph, “Its essential to remember that if somebody sends you a message or e-mail unsolicited, they likely want something from you. These links and accessories can consist of malware designed to take your keys or get to your systems,” continuing:”Furthermore, they can redirect you to phishing websites. Constantly confirm the senders identity and the e-mails authenticity to guarantee security. Avoid clicking on links straight; copy and paste the URL into your internet browser, examining carefully for any spelling inconsistencies in the domain.”By impersonating assistance workers, fraudsters make use of users trust in genuine customer assistance channels. In addition, they prey on the desire to solve concerns rapidly, leading users to willingly reveal their personal info, which scammers can utilize for destructive functions later.Fake websites and cloned platformsMalicious stars can also build fake sites and platforms to draw in unwary users.Domain name spoofing is a strategy where fraudsters sign up domain names that closely resemble the names of legitimate cryptocurrency exchanges or wallet companies. For example, they may sign up a domain like “exchnage.com” instead of “exchange.com” or “myethwallet” instead of “myetherwallet.” These minor variations can be quickly ignored by unwary users.Lahav said that users ought to “verify whether the website in concern is trusted and popular.”Recent: Bitcoin is on a clash with Net Zero guarantees”Checking the right spelling of the URL is also important, as malicious stars typically produce URLs that carefully resemble those of genuine sites. Users must likewise be mindful with sites they discover through Google ads, as they might not naturally rank high in search results page,” he said.Scammers utilize these spoofed domain names to produce sites that mimic genuine platforms. They typically send phishing e-mails or messages consisting of links to these fake sites, tricking users into thinking they are accessing the genuine platform. Once users enter their login credentials or perform transactions on these websites, the fraudsters capture the sensitive info and exploit it for their gain.Malicious software and mobile appsHackers can likewise turn to utilizing destructive software to target users. Keyloggers and clipboard hijacking are strategies crypto phishing fraudsters utilize to take sensitive information from users devices.Keyloggers are destructive software application that tape-record every keystroke a user makes on their device. The keylogger captures this information and sends it back to the fraudsters when users enter their login credentials or private keys. Clipboard hijacking involves intercepting the material copied to the devices clipboard. Cryptocurrency deals frequently include copying and pasting wallet addresses or other delicate details. Scammers utilize harmful software application to keep track of the clipboard and replace genuine wallet addresses with their own. When users paste the info into the designated field, they unwittingly send their funds to the scammers wallet instead.How users can stay secured against crypto phishing scamsThere are steps that users can take to secure themselves while navigating the crypto space.Enabling two-factor authentication (2FA) is one tool that can help protect crypto-related accounts from phishing rip-offs. 2FA includes an extra layer of defense by needing users to provide a 2nd form of confirmation, normally a distinct code produced on their mobile phone, in addition to their password. This guarantees that even if opponents obtain the users login credentials through phishing attempts, they still need the second element (such as a time-based one-time password) to acquire access.Utilizing hardware or software-based authenticatorsWhen establishing 2FA, users must think about utilizing hardware or software-based authenticators rather than relying exclusively on SMS-based authentication. SMS-based 2FA can be vulnerable to SIM-swapping attacks, where assaulters fraudulently take control of the users phone number.Hardware authenticators, such as YubiKey or security secrets, are physical gadgets that create one-time passwords and provide an additional layer of security. Software-based authenticators, such as Google Authenticator or Authy, create time-based codes on users smart devices. These methods are securer than SMS-based authentication because they are not prone to SIM-swapping attacks.Verify site authenticityTo safeguard versus phishing scams, users ought to prevent clicking on links provided in e-mails, messages or other unproven sources. Instead, they ought to by hand enter the website URLs of their cryptocurrency exchanges, wallets or any other platforms they wish to access.By by hand entering the website URL, users ensure they access the legitimate website straight instead of being redirected to a phony or cloned website by clicking a phishing link.Be cautious with links and attachmentsBefore clicking any links, users should hover their mouse cursor over them to see the destination URL in the internet browsers status bar or tooltip. This enables users to verify the links real destination and ensure that it matches the expected website.Phishing scammers often disguise links by showing a various URL text than the location. By hovering over the link, users can identify disparities and suspicious URLs that might suggest a phishing attempt.Parker explained to Cointelegraph, “Its extremely easy to fake the underlying link in an email. A fraudster can reveal you one link in the e-mails text but make the underlying link something else.” “A preferred rip-off amongst crypto phishers is to copy a credible sites UI however put their harmful code for the login or Wallet Connect part, which leads to stolen passwords, or worse, stolen seed expressions. So, always confirm the website URL youre logging into or linking your crypto wallet with.”Scanning accessories with anti-virus softwareUsers need to exercise care when downloading and opening accessories, specifically from suspicious or untrusted sources. Accessories can include malware, including keyloggers or trojans, which can jeopardize the security of a users gadget and cryptocurrency accounts.To mitigate this danger, users should scan all accessories with trustworthy antivirus software prior to opening them. This helps identify and eliminate any possible malware hazards, reducing the possibilities of succumbing to a phishing attack.Keep software and apps updatedKeeping operating systems, web browsers, devices and other software application up to date is essential for preserving the security of the users devices. Updates can consist of security spots that address understood vulnerabilities and protect versus emerging threats.Utilizing reputable security softwareTo include an additional layer of protection against phishing scams and malware, users should think about setting up trustworthy security software on their devices. Antivirus, anti-phishing and anti-malware software application can help detect and obstruct destructive threats, including phishing e-mails, fake sites and malware-infected files.By regularly updating and running security scans using credible software application, users can minimize the risk of falling victim to phishing rip-offs and guarantee the overall security of their gadgets and cryptocurrency-related activities.Educate yourself and stay informedCrypto phishing rip-offs continuously evolve, and brand-new methods emerge regularly. Users must take the effort to inform themselves about the latest phishing techniques and frauds targeting the cryptocurrency neighborhood. In addition, stay notified by investigating and checking out about current phishing incidents and security best practices.Recent: What is fair use? United States Supreme Court weighs in on AIs copyright dilemmaTo stay upgraded on security-related news and receive timely cautions about phishing frauds, users need to follow trusted sources in the cryptocurrency neighborhood. This can include main announcements and social networks accounts of cryptocurrency exchanges, wallet companies and respectable cybersecurity organizations.By following trusted sources, users can get precise information and alerts relating to emerging phishing scams, security vulnerabilities and finest practices for protecting their crypto assets.
Keyloggers and clipboard hijacking are techniques crypto phishing fraudsters use to take delicate information from users devices.Keyloggers are harmful software application programs that tape-record every keystroke a user makes on their gadget. When users paste the info into the desired field, they unwittingly send their funds to the scammers wallet instead.How users can stay secured versus crypto phishing scamsThere are steps that users can take to protect themselves while browsing the crypto space.Enabling two-factor authentication (2FA) is one tool that can assist protect crypto-related accounts from phishing rip-offs. These methods are securer than SMS-based authentication due to the fact that they are not prone to SIM-swapping attacks.Verify website authenticityTo secure against phishing scams, users need to prevent clicking on links supplied in e-mails, messages or other unproven sources. Rather, they must manually get in the website URLs of their cryptocurrency exchanges, wallets or any other platforms they want to access.By by hand going into the site URL, users ensure they access the legitimate site directly rather than being rerouted to a phony or cloned site by clicking on a phishing link.Be mindful with links and attachmentsBefore clicking on any links, users must hover their mouse cursor over them to view the location URL in the internet browsers status bar or tooltip. Accessories can contain malware, including trojans or keyloggers, which can compromise the security of a users device and cryptocurrency accounts.To alleviate this threat, users ought to scan all attachments with reputable anti-viruses software prior to opening them.
Related Content
- Honor Veterans Day By Adopting Bitcoin And Ending Forever War Funding
- KYC hook for Uniswap v4 stirs community controversy
- Deribit’s Bitcoin volatility index hits lifetime lows, hinting sideways action
- Bitcoin traders hope to ‘buy the dip’ as BTC price heads toward $30K
- China dev fined 3 yr’s salary for VPN use, 10M e-CNY airdrop: Asia Express