Chibi Finance $1M alleged rug pull: How it happened
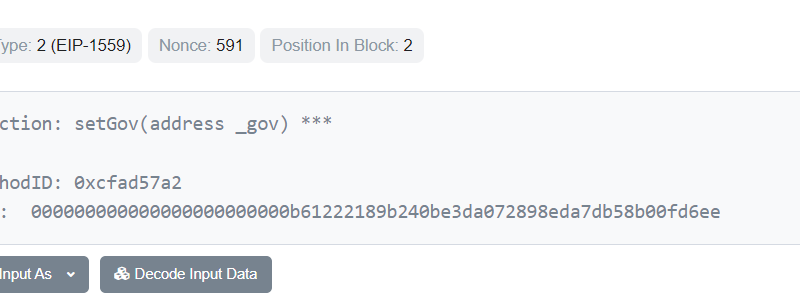
Here is an explanation of how it works, with StrategySushiSwap.sol being utilized as an example: Lines 340– 343 of StrategySushiSwap.sol state that if the panic() function is called, it will call a 2nd function called “emergencyWithdraw” on the ISushiStake contract.The panic() function in StrategySushiSwap.sol contract. A user might want to call this function if a bug in the reward contract triggers them not to be able to get rewards.The emergencyWithdraw function has a failsafe to avoid use by unauthorized persons. A problem can develop if the user does not call this function directly from their own wallet.For example, when a user deposited funds utilizing Chibi Finance, their crypto was sent out to SushiSwap by the StrategySushiSwap contract, not by the end-user directly. CertiK speculated that each of these transactions might have added a Chibi Finance contract to a list within the harmful agreements data for a total of eight agreements in the list.On June 27, the deployer account for Chibi Finance moved admin rights for the 8 Chibi Finance agreements to the harmful contract. It did this through 8 separate deals, each one calling the “setGov” function on a specific contract.Admin rights for one of the Chibi Finance agreements being changed.
On June 26, decentralized finance (DeFi) aggregator Chibi Finance was exploited by its own deployer account, and $1 million worth of cryptocurrency was drained pipes from its agreements in an evident carpet pull or exit scam. The procedures official interface vanished, producing a 404 error, and all social media for the app was removed. After the funds were drained pipes, they were swapped for Wrapped Ether (WETH) and bridged to Ethereum, where they were afterward sent out to Tornado Cash by the attacker.The rate of the Chibi Finance (CHIBI) governance token fell by over 90% as the news broke.CHIBI token rate. Source: CoinGecko.But “rug pulls” should not be possible in DeFi. After all, these apps, by definition, dont run on centralized facilities. So the apps developer shouldnt have the ability to run off with everyones crypto or cash. For this reason, it might be helpful to evaluate how the alleged fraud was pulled off.CertiK has actually produced a detailed report after examining the event. When combined with blockchain data, this report can clarify how the attack happened and what users can do to secure themselves against similar attacks or frauds in the future. The Chibi Finance appBefore its user interface went offline, Chibi described itself as “the most popular yield aggregator on Arbitrum.” It declared to allow users to acquire yield from throughout the Arbitrum community. According to CertiK, the DeFi aggregator has actually been growing in overall worth locked (TVL)– a measurement of the worth of crypto held in an apps agreements– since it launched in April. On June 21, Chibi revealed it had attained $500,000 in TVL. At the time, the group stated a goal to reach $1 million. On June 26, the app was noted on CoinGecko for the very first time, providing it higher exposure. It seems to have reached its $1 million goal soon after this event, right prior to the tokens were drained from its contracts. As a result, financiers lost over $1 million worth of crypto in the attack or scam.Chibi Finance contractsThe attack made use of a loophole in 8 different agreements utilized in the Chibi Finance procedure. These contracts were forked from other jobs and were not special to Chibi. One of them was StrategyAave.sol at Arbitrum address 0x45E8a9BA6Fcd612a30ae186F3Cc93d78Be3E7d8d, which has likewise been deployed to several other addresses on Abitrum, Ethereum, the BNB Smart Chain and other networks. Another example is the StrategySushiSwap.sol contract at 0x9458Ea03af408cED1d919C8866a97FB35D06Aae0. This likewise has several variations on Arbitrum and other networks.These agreements seem commonly utilized in DeFi aggregator applications, not simply Chibi Finance.Related: DeFi aggregation: Paving the way for mass adoptionPanic functionBlockchain information exposes that some of the agreements used by Chibi Finance contain a “panic” function that can be utilized to withdraw all tokens from a swimming pool and send them to a specific address. This function was essential to the opponents technique. Here is a description of how it works, with StrategySushiSwap.sol being utilized as an example: Lines 340– 343 of StrategySushiSwap.sol state that if the panic() function is called, it will call a second function named “emergencyWithdraw” on the ISushiStake contract.The panic() function in StrategySushiSwap.sol contract. Source: Blockchain data.The ISushiStake contract, in turn, is simply an interface. It includes no executable code. Instead, it points to the SushiSwap: MiniChefV2 agreement at 0xF4d73326C13a4Fc5FD7A064217e12780e9Bd62c3. The MiniChefV2 address is listed as a main contract for the decentralized exchange, SushiSwap. So the “panic” function calls an “emergencyWithdraw” function within SushiSwap.At the SushiSwap address, the emergencyWithdraw function can be seen on lines 626– 643. SushiSwap MiniChefV2 emergencyWithdraw function. Source: Blockchain data.This function permits the owner of funds to withdraw without taking benefits. This might work in an emergency situation. A user might desire to call this function if a bug in the reward agreement triggers them not to be able to get rewards.The emergencyWithdraw function has a failsafe to avoid usage by unapproved persons. It specifies on line 360, “UserInfo storage user = userInfo [pid] [msg.sender],” indicating that the “user” is defined as the sender of the message. Under regular situations, this ought to allow a user to emergency-withdraw their own funds, but not funds belonging to anyone else. There does not appear to be anything harmful about this function in SushiSwap. However, an issue can develop if the user does not call this function straight from their own wallet.For example, when a user deposited funds using Chibi Finance, their crypto was sent to SushiSwap by the StrategySushiSwap agreement, not by the end-user straight. This indicated that the Chibi Finance app was recognized as the “user” when trying to emergency-withdraw funds. This, in turn, permitted Chibi to withdraw the users funds on users behalf.Related: How to spot a rug pull in DeFi: 6 suggestions from CointelegraphHowever, the funds must have still been safe as long as the panic function might only be called by the end-user. Regrettably, the panic function does not have this requirement. Rather, it is simply listed within the Chibi Finance contract as an “onlyGov” function, implying that an admin can call it, however nobody else. The assailant depended on this loophole to perform their attack.How the Chibi Finance attack was carried outAccording to the CertiK report, Ethereum username Shadowout.eth withdrew 10 Ether (ETH) from Tornado Cash on June 15. These funds were bridged to Arbitrum, and 0.2 ETH was sent from this user to deal with 0x80c1ca8f002744a3b22ac5ba6ffc4dc0deda58e3. This second account then created a destructive contract on June 23 at address 0xb61222189b240be3da072898eda7db58b00fd6ee. The assailant called the “include swimming pool” function on this malicious agreement 8 times on June 23. Because the contract is unproven, the code for this “add pool” function is unidentified. CertiK hypothesized that each of these deals might have included a Chibi Finance contract to a list within the harmful agreements information for a total of eight contracts in the list.On June 27, the deployer account for Chibi Finance moved admin rights for the eight Chibi Finance agreements to the harmful contract. It did this through eight separate transactions, every one calling the “setGov” function on a particular contract.Admin rights for one of the Chibi Finance agreements being changed. Source: Blockchain data.After the harmful contract gained these governance rights, its creator called its “execution” function. This triggered it to call “panic” on each of the eight agreements, which in turn called “emergencyWithdraw” on related swimming pools in DeFi apps such as SushiSwap, Aave and Global Hectare.The result was that all of the funds transferred by users to these swimming pools through Chibi Finance were drained pipes by the assaulter, leading to losses of over $1 million to investors.How can Chibi-style carpet pulls be avoided?Given that the attack counted on a “panic” function that enabled an admin to drain pipes all of the users funds, one method to avoid a Chibi-style carpet pull would be not to use apps that have this function. On the other hand, if an aggregator does not have a “panic” function, there is a danger that the users funds might get stuck if a bug or make use of is found within the aggregator app. Users may desire to consider these tradeoffs if they choose to utilize aggregator apps rather of directly connecting with the underlying pools.Related: Over $204M was lost in Q2 DeFi hacks and frauds: ReportDeFi users may likewise desire to think about that wise agreement code can be exceptionally complicated, and it might not be possible for most users to determine by themselves whether an app has a security flaw. As CertiK declared in its report:”The Chibi Finance event shows the risks that are connected with centralization in the Web3 area. […] It is an impractical expectation for regular investors to find and comprehend the centralization risks within tasks like Chibi Finance by just doing their own research.”For this reason, users may desire to examine an apps published audits before utilizing it, CertiK stated.Chibi Finance declared to be examined by blockchain security firm SolidProof. The contents of the supposed audit are no longer available, as the projects GitHub has been taken down and was never ever conserved by internet archives. Cointelegraph could not figure out whether the threats posed by the “panic” function were disclosed in the audit report or perhaps whether an audit took place.Cointelegraph has actually connected to SolidProof for comment however did not receive a reply by publication.Rug pulls or exit rip-offs have actually ended up being a common problem in the DeFi space. On June 1, blockchain security company Beosin reported that over $45 million was lost from rug draws in May, exceeding routine DeFi exploits. In April, the Ordinals Finance protocol was likewise presumably rugged for $1 million through a “safuToken” transfer function.
Related Content
- ‘Elegant and ass-backward’: Jameson Lopp’s first impression of Bitcoin
- 3 Bitcoin price metrics showing ‘insane’ similarities to 2020 breakout
- Cryptocurrency Myths Debunked: Sorting Fact from Fiction in the Digital Currency Realm
- Binance dubs barred Russian banks on its platform as ‘Yellow’ and ‘Green’ cards
- Gemini files brief in lawsuit against SEC, requests to keep it simple