Breaking: Curve Finance pools exploited in over $47M due to reentrancy vulnerability
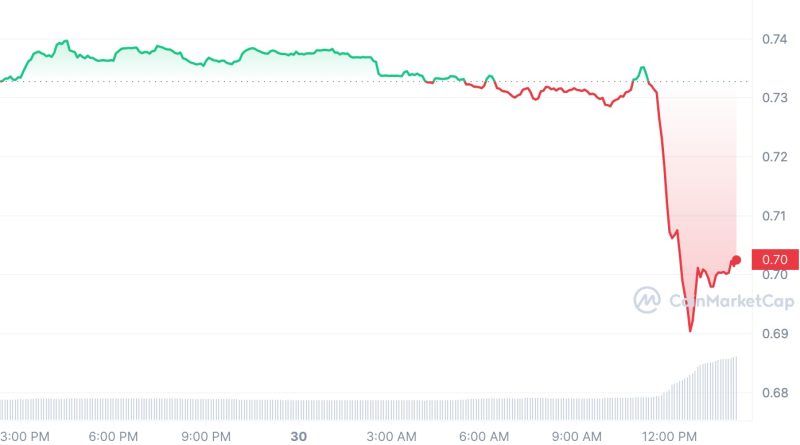
The exploit triggered panic throughout the DeFi environment, prompting a wave of deals throughout pools and a rescue operation from white hats. According to Curve Finance, crvUSD contracts and any pools with it were not impacted by the attack. Curve DAO token prince on July 30, 2023.
Thank you for reading this post, don't forget to subscribe!
Update (July 30, at 7:55 pm UTC): This post has actually been upgraded to supply more details about the exploitSeveral stable pools on Curve Finance using Vyper were made use of on July 30, with losses reaching over $47 million.” The examination is continuous however any job relying on these variations must instantly reach out to us,” Vyper composed on X. Based on an analysis of affected contracts by security firm Ancilia, 136 agreements used Vyper 0.2.15 with reentrant security, 98 agreements used Vyper 0.2.16 and 226 agreements used Vyper 0.3.0. A number of stablepools (alETH/msETH/pETH) utilizing Vyper 0.2.15 have actually been exploited as a result of a malfunctioning reentrancy lock.
Update (July 30, at 7:55 pm UTC): This short article has actually been updated to provide more information about the exploitSeveral stable pools on Curve Finance utilizing Vyper were made use of on July 30, with losses reaching over $47 million.” The examination is continuous however any project relying on these variations need to right away reach out to us,” Vyper wrote on X. Based on an analysis of afflicted contracts by security company Ancilia, 136 agreements used Vyper 0.2.15 with reentrant defense, 98 agreements utilized Vyper 0.2.16 and 226 contracts used Vyper 0.3.0. A number of stablepools (alETH/msETH/pETH) utilizing Vyper 0.2.15 have been exploited as a result of a malfunctioning reentrancy lock. Decentralized exchange Ellipsis reported that a little number of stable pools with BNB were made use of using an old Vyper compiler.
According to initial investigation, some versions of the Vyper compiler do not properly implement the reentrancy guard, which prevents numerous functions from being executed at the very same time by locking an agreement. Reentrancy attacks can potentially drain all funds from a contract.Vyper is a contract-oriented, pythonic shows language that targets the Ethereum Virtual Machine (EVM). Vyper resemblances to Python makes the language one of the beginning points for Python designers jumping into Web3. A number of decentralized finance projects were impacted by the attack. Decentralized exchange Ellipsis reported that a small number of stable swimming pools with BNB were made use of using an old Vyper compiler. Alchemixs alETH-ETH also saw $13.6 million outflow, along with $11.4 million exploited on JPEGds pETH-ETH pool, and $1.6 million in Metronomes sETH-ETH pool. Curving Finance CEO Michael Egorov later on verified 32 million CRV tokens worth over $22 million had been drained pipes from the swap swimming pool in a Telegram channel.Certain kind of Curve factory pool is coming across read-only reentrancy attack and causing a total loss of $11m( @JPEGd_69) + $13m( @AlchemixFi) + … Initial examination founds that vyper compiler (0.2.15) does not execute the reentrancy guard properly. add_liquidity and … pic.twitter.com/avaHdtSFsm— Tony KΞ (@tonyke_bot) July 30, 2023