Breaking: Curve Finance pools exploited by over $47M due to reentrancy vulnerability
Update (July 30, at 7:55 pm UTC): This post has actually been upgraded to provide more details about the exploitSeveral stable pools on Curve Finance using Vyper were made use of on July 30, with losses reaching over $47 million.” The investigation is ongoing however any project relying on these variations ought to right away reach out to us,” Vyper wrote on X. Based on an analysis of affected contracts by security firm Ancilia, 136 agreements utilized Vyper 0.2.15 with reentrant defense, 98 contracts used Vyper 0.2.16 and 226 agreements utilized Vyper 0.3.0. A number of stablepools (alETH/msETH/pETH) using Vyper 0.2.15 have been made use of as a result of a malfunctioning reentrancy lock. Decentralized exchange Ellipsis reported that a small number of steady pools with BNB were exploited using an old Vyper compiler.
Thank you for reading this post, don't forget to subscribe!
Update (July 30, at 7:55 pm UTC): This post has actually been upgraded to supply more details about the exploitSeveral stable pools on Curve Finance utilizing Vyper were made use of on July 30, with losses reaching over $47 million. According to Vyper, its 0.2.15, 0.2.16 and 0.3.0 versions are susceptible to malfunctioning reentrancy locks. ” The investigation is ongoing but any project relying on these versions must right away connect to us,” Vyper composed on X. Based on an analysis of affected agreements by security firm Ancilia, 136 contracts used Vyper 0.2.15 with reentrant defense, 98 contracts used Vyper 0.2.16 and 226 contracts utilized Vyper 0.3.0. A number of stablepools (alETH/msETH/pETH) using Vyper 0.2.15 have actually been exploited as a result of a malfunctioning reentrancy lock. We are examining the circumstance and will update the community as things develop.Other pools are safe. https://t.co/eWy2d3cDDj— Curve Finance (@CurveFinance) July 30, 2023
According to preliminary investigation, some versions of the Vyper compiler do not correctly carry out the reentrancy guard, which avoids multiple functions from being performed at the exact same time by locking an agreement. Decentralized exchange Ellipsis reported that a small number of stable swimming pools with BNB were exploited utilizing an old Vyper compiler. Curve Finance CEO Michael Egorov later on verified 32 million CRV tokens worth over $22 million had actually been drained pipes from the swap swimming pool in a Telegram channel.Certain type of Curve factory pool is coming across read-only reentrancy attack and triggering an overall loss of $11m( @JPEGd_69) + $13m( @AlchemixFi) + … Initial investigation establishes that vyper compiler (0.2.15) does not carry out the reentrancy guard properly.
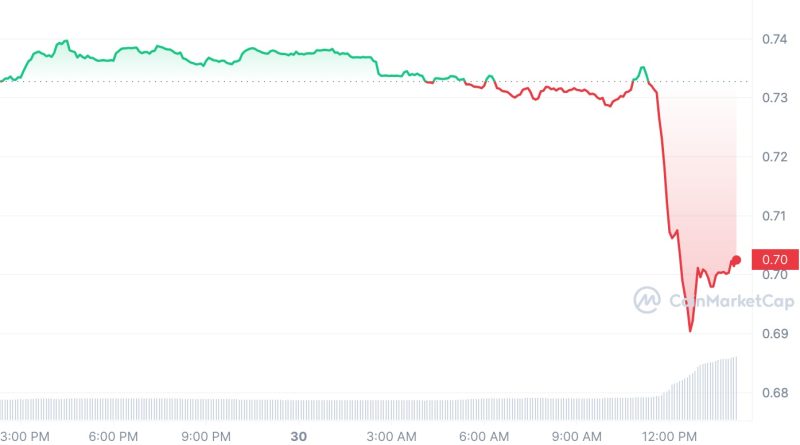
The exploit triggered panic throughout the DeFi community, triggering a wave of deals across pools and a rescue operation from white hats. Data from CoinMarketCap reveals Curve Finances energy token Curve DAO (CRV) decreasing over 5% in reaction to the news. CRVs liquidity has decreased significantly in recent months, making it vulnerable to violent price swings, Cointelegraph reported. According to Curve Finance, crvUSD contracts and any swimming pools with it were not affected by the attack. Curve DAO token prince on July 30, 2023. Source: CoinMarketCapCurve Finance is a DeFi protocol that allows the decentralized exchange of stablecoins within Ethereum. The procedure has been targeted by a series of occurrences within its community. Simply a few days ago, its omnipool platform Conic Finance was exploited for $3.26 million in Ether (ETH), with nearly the entire quantity stolen sent out to a brand-new Ethereum address in simply one transaction.DeFi procedures have actually been targeted by numerous attacks over the past months. According to a report by Web3 portfolio app De.Fi, more than $204 million was tricked through DeFi hacks and rip-offs in the 2nd quarter of 2023 alone.Magazine: Should crypto tasks ever work out with hackers? Probably