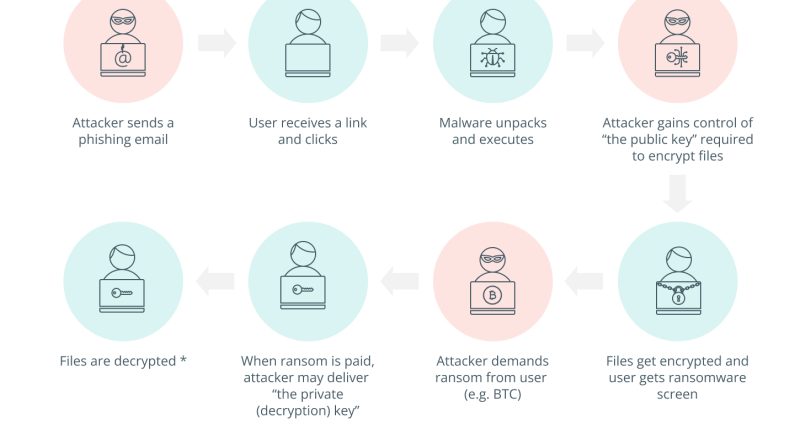
The anatomy of a cyberattack
Attackers utilize a range of techniques to contaminate unsuspecting victims with malware, consisting of phishing emails, harmful links, contaminated attachments and watering hole assaults.ExploitationDuring this phase, assailants use the flaws in the target network or system to obtain unapproved gain access to. After deploying the RAT on a jeopardized system, the assailant can send commands to the RAT and recover data in response.The aggressors frequently impersonate relied on entities, such as banks, online services or colleagues, to acquire the victims trust and control them into taking specific actions that compromise their security. The assaulters require a ransom payment from the victim to offer the decryption key or bring back access to the encrypted data.Reconnaissance: Attackers determine possible victims based on their vulnerabilities, frequently through automated scans of open ports and exposed services.Weaponization: Cybercriminals plan ransomware into destructive software application that secures the victims information and demand a ransom for its release.Delivery: The ransomware is provided via various approaches, such as contaminated e-mail attachments or harmful websites.Exploitation: Once the victims system is infected, the ransomware makes use of software application vulnerabilities to secure the files and render them inaccessible.Installation: The ransomware gains perseverance on the victims system, making it difficult to remove without the decryption key.C2: Ransomware interacts with the opponents server to offer the decryption secret after the ransom is paid.Actions on objective: The objective is to obtain the victim by demanding a ransom payment in exchange for the decryption secret to recover the encrypted data.Covering tracks: Ransomware aggressors often cover their tracks by using encryption and anonymizing innovations to prevent detection.Understanding the anatomy of a cyberattack is vital to developing effective cybersecurity procedures.
Thank you for reading this post, don't forget to subscribe!
Attackers employ a variety of techniques to contaminate unwary victims with malware, including phishing emails, damaging links, contaminated attachments and watering hole assaults.ExploitationDuring this phase, assaulters utilize the defects in the target network or system to acquire unauthorized gain access to. After deploying the RAT on a compromised system, the enemy can send commands to the RAT and recover information in response.The enemies often impersonate relied on entities, such as banks, online services or colleagues, to get the victims trust and control them into taking particular actions that compromise their security. The aggressors require a ransom payment from the victim to supply the decryption key or restore access to the encrypted data.Reconnaissance: Attackers recognize prospective victims based on their vulnerabilities, frequently through automated scans of open ports and exposed services.Weaponization: Cybercriminals package ransomware into malicious software that secures the victims data and require a ransom for its release.Delivery: The ransomware is delivered through numerous techniques, such as contaminated e-mail accessories or harmful websites.Exploitation: Once the victims system is contaminated, the ransomware exploits software application vulnerabilities to secure the files and render them inaccessible.Installation: The ransomware gains determination on the victims system, making it difficult to eliminate without the decryption key.C2: Ransomware interacts with the assailants server to supply the decryption key after the ransom is paid.Actions on goal: The goal is to extort the victim by requiring a ransom payment in exchange for the decryption secret to recover the encrypted data.Covering tracks: Ransomware opponents typically cover their tracks by utilizing encryption and anonymizing technologies to prevent detection.Understanding the anatomy of a cyberattack is crucial to establishing effective cybersecurity steps.
Related Content
- Is ‘Uptober’ here? Bitcoin, Ethereum suddenly pump, wiping $70M in shorts
- Navigating Market Volatility: Strategies for Successful Crypto Trading
- Mauritius mulls wrapping metaverse into financial services
- The Future of Money: How Cryptocurrency Will Change the Way We Think About Finances
- Mining Bitcoin With Energy Stored In Waste Tires