CoinsPaid claims North Korean hacking group used fake job interview to steal $37M
Estonia-based cryptocurrency payments firm CoinsPaid suspects North Korean hackers with the Lazarus Group got access to its systems through fake recruiters targeting employees.In an Aug. 7 blog post, CoinsPaid said an exploit which enabled hackers to take more than $37 million on July 22 was the result of tricking one employee into downloading software during a fake job interview, having them think they were completing a technical task. The firm reported that the employee responded to a job offer put out by hackers and downloaded the destructive code, permitting the bad actors to steal information and offer them access to CoinsPaids infrastructure.” Having gotten access to the CoinsPaid infrastructure, the opponents took advantage of a vulnerability in the cluster and opened a backdoor,” said CoinsPaid.
Thank you for reading this post, don't forget to subscribe!
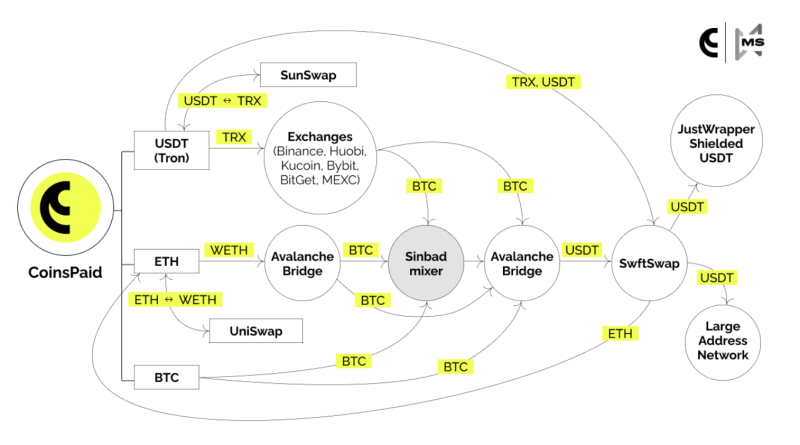
Related: Curve hacker behind $61M break-in starts returning fundsIn its July 26 post-mortem report of the hack, CoinsPaid stated it believed Lazarus Group. Prior to the $37-million exploit, the hackers had actually made several efforts to penetrate the platform starting in March 2023, but switched their method to “vigorous and highly sophisticated social engineering techniques” after several failures– targeting specific employees rather than the business itself.Tracing the funds stolen from CoinsPaid on July 22. Source: CoinsPaidCoinsPaid said it had partnered with blockchain security company Match Systems to track the stolen funds, the majority of which were transferred to SwftSwap. According to the company, many elements of the hackers deals mirrored those of the Lazarus Group, as in the $35-million hack of Atomic Wallet in June. The business was continuing to monitor any movement of the funds since Aug. 7. Magazine: Should crypto projects ever negotiate with hackers? Probably
Related Content
- Binance starts BTC/FDUSD and ETH/FDUSD trading pairs with zero-fees
- Chainlink leads the market with 61% weekly gain — What’s driving LINK price?
- India G20 confirms ‘active discussions’ around global crypto framework
- Security or not, Ether looks poised to hold the $1.8K level based on 3 key metrics
- TeraWulf increases self-mined BTC in Q2, while Hut8 looks to USBTC merger