Breaking: ‘All funds are at risk’ — Steadefi exploited in ongoing attack
The aggressor supposedly took the private secret to the groups deployer wallet, giving access to carry out ownerOnly functions.”All loanable funds have been drained by the assailant. On Aug. 4, the Curve procedure was made use of for $61 million, although the opponent later on started returning some of the funds.
Thank you for reading this post, don't forget to subscribe!
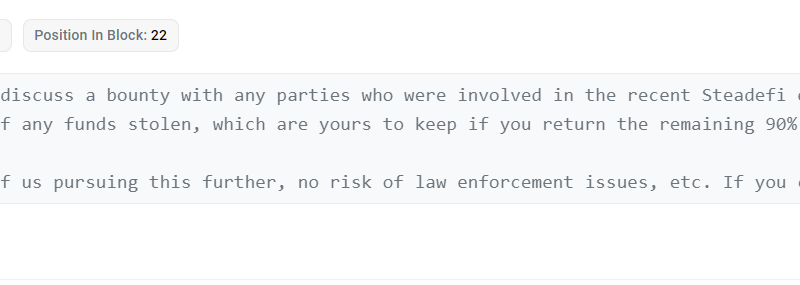
Decentralized financing (DeFi) app Steadefi was exploited for at least $334,000 on Aug. 7 in an ongoing attack. The apps development group stated in a social media post that the attack presently “puts all funds at danger.” The apps total worth locked has dropped as an outcome of the attack, according to data from DefiLlama.Steadefi overall value locked. Source: DefiLlamaThe Steadefi group posted a message to X– previously Twitter– specifying: “NOTICE: Steadefi has actually been made use of and all funds are presently at danger.” The group likewise verified that an on-chain message has actually been sent to attend to 0x9cf71F2ff126B9743319B60d2D873F0E508810dc on Ethereum in an attempt to work out with the assaulter. Blockchain data exposes that a variety of large inflows entered this address on the Avalanche chain, starting at 4:41 pm UTC. The tokens transferred to the address consist of 130,429 USD Coin (USDC), 3.39 Bitcoin (BTC), 15 Wrapped Ether (WETH) and 6,184 Avalanche (AVAX). Aside from the WETH, all other tokens were instantly switched for WETH. The alleged assailant then bridged 184 WETH onto another network through the Synapse bridge.The address likewise appears to have performed a comparable series of transactions on the Arbitrum network.Ethereum blockchain data reveals that the development group has sent a message to the attacker, offering to let the hacker keep 10% of the supposedly taken funds.Related: Curve-Vyper exploit: The whole story so far.Steadefi sends out message to enemy. Source: EtherscanAfter the Steadefi team verified the attack, it published a follow-up message to X describing how the attack had actually taken place. The enemy reportedly stole the personal key to the teams deployer wallet, giving access to perform ownerOnly functions. The exploiter then “went on to take numerous owner-only actions such as allowing any wallet to be able to obtain any available funds from the lending vaults.”All loanable funds have been drained pipes by the attacker. Security held in vaults and not lent out has not been drained pipes due to the fact that the app does not consist of an ownerOnly function to eliminate deposits. As an outcome, users who deposited to the “technique” vaults may still be able to withdraw at least some of their funds. On the other hand, the opponent paused farming contracts using an ownerOnly function. Therefore, users who deposited ibtokens or svtokens to farms can not withdraw, and their funds are basically stuck inside the apps agreements. According to the post, the majority of holders of these tokens have actually transferred into the farms and can not withdraw.Exploits have actually been a continuing problem in the DeFi space. On Aug. 8, Estonia-based crypto payment firm CoinsPaid stated aggressors stole $37 million through a phony task interview. On Aug. 4, the Curve protocol was exploited for $61 million, although the aggressor later on started returning a few of the funds.
Related Content
- Axie Infinity developer brings Japanese Web2 games to Ronin
- 3AC liquidators file motion to hold Kyle Davies in contempt
- Bitcoin ‘short squeeze’ sends BTC price to $35.9K as OI stays elevated
- Tapsigner Bitcoin Hardware Wallet: Security Meets Convenience?
- Binance Labs invests in ARKM, the native token of Arkham platform