Darknet bad actors work together to steal your crypto, here’s how — Binance CSO
Lurking in the shadiest corners of the dark web is a “well-established” ecosystem of hackers that target cryptocurrency users with bad “security hygiene,” according to Binances chief security officer.Speaking to Cointelegraph, Binance CSO Jimmy Su said in current years, hackers have actually moved their gaze towards crypto end-users. Here, bad stars gather and collate ill-gotten intel about crypto users, creating entire spreadsheets filled with information about different users. Created documents, typically used by hackers to open accounts on crypto trading websites can likewise be purchased on the dark web.Data refinersAccording to Su, the data gathered is then sold downstream to another group– typically made up of data engineers that specialize in refining data. Su explained this could involve leaving the funds inactive for years and then moving them to a crypto mixer such as Tornado Cash.Related: Arbitrum-based Jimbos Protocol hacked, losing $7.5 M in Ether” There are groups that we understand that may sit on their stolen gains for two, three years without any motion,” included Su. While not much can stop crypto hackers, Su urges crypto users to practice better “security health.
Hiding in the shadiest corners of the dark web is a “well-established” environment of hackers that target cryptocurrency users with bad “security hygiene,” according to Binances primary security officer.Speaking to Cointelegraph, Binance CSO Jimmy Su said in recent years, hackers have shifted their look toward crypto end-users. Su kept in mind when Binance initially opened in July 2017, the group saw plenty of hacking efforts on its internal network.
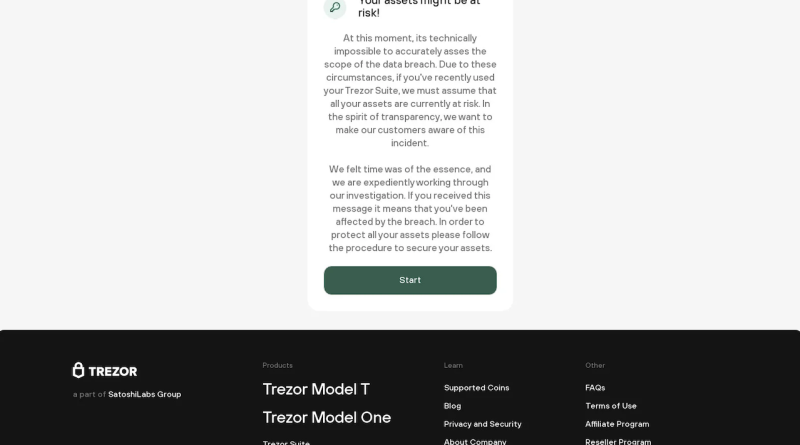
In April, a research paper by Privacy Affairs exposed cybercriminals have been offering hacked crypto represent as little as $30 a pop. Forged paperwork, frequently utilized by hackers to open accounts on crypto trading sites can likewise be purchased on the dark web.Data refinersAccording to Su, the information collected is then sold downstream to another group– normally comprised of information engineers that focus on refining information.” For example, there was an information set in 2015 for Twitter users. […] Based on the details there, they can even more fine-tune it to see based on the tweets to see which ones are actually crypto-related.” These information engineers will then use “bots and scripts” to find out which exchanges the crypto enthusiast may be signed up with.They do this by trying to produce an account with the users email address. If they get an error that states the address is currently in use, then theyll know if they use the exchange– this might be important information that might be used by more targeted frauds, stated Su. Hackers and phishersThe 3rd layer is generally what develops headings. Phishing scammers or hackers will take the previously refined data to develop “targeted” phishing attacks. “Because now they know Tommy is a user of exchange X, they can simply send an SMS stating, Hey Tommy, we found someone withdrew $5,000 from your account, please reach and click this link client service if it wasnt you.” In March, hardware wallet company Trezor warned its users about a phishing attack developed to take investors money by making them go into the wallets healing phrase on a phony Trezor website.The phishing project involved assaulters positioning as Trezor and calling victims via phone e-mails, texts, or calls declaring that there has been a security breach or suspicious activity on their Trezor account.A screenshot from a phishing domain copying Trezors website. Source: Bleeping ComputerGetting away with itOnce the funds are stolen, the last action is getting away with the break-in. Su explained this could involve leaving the funds inactive for years and after that moving them to a crypto mixer such as Tornado Cash.Related: Arbitrum-based Jimbos Protocol hacked, losing $7.5 M in Ether” There are groups that we know that may rest on their taken gains for two, three years without any motion,” included Su. While not much can stop crypto hackers, Su prompts crypto users to practice better “security hygiene.” This might involve withdrawing authorizations for decentralized financing tasks if they no longer utilize them, or making sure interaction channels such as e-mail or SMS that are utilized for two-factor authentication are kept personal. Publication: Tornado Cash 2.0– The race to construct legal and safe coin mixers
” Hackers always choose the most affordable bar to attain their objectives, due to the fact that for them its an organization. The hacker community is a reputable ecosystem.” According to Su, this community consists of 4 distinct layers– intelligence gatherers, data refiners, hackers and cash launderers. Data gatherersThe most upstream layer is what Su explained as “risk intelligence.” Here, bad stars collect and look at ill-gotten intel about crypto users, developing whole spreadsheets filled with information about different users. This could include crypto sites a user often visits, what e-mails they utilize, their name, and whether theyre on Telegram or social networks.” There is a market for this on the dark web where this information is sold […] that describes the user,” described Su in a May interview.Su noted this information is generally collected wholesale, such as previous customer info leakages or hacks targeting other suppliers or platforms. An employee of our e-mail vendor, https://t.co/6vM4WAcJal, misused their worker access to download & & share e-mail addresses with an unapproved external party. Email addresses offered to OpenSea by users or newsletter customers were impacted.https:// t.co/ Osb6qqkqZZ– OpenSea (@opensea) June 30, 2022
Related Content
- Another week of DeFi hacks, but ZK-proof development heats up: Finance Redefined
- Crypto Aid Israel raises $185K in 10 days, distributes aid to 4 organizations
- Bitcoin dominance hits 54% — Highest in 2.5 years as BTC halving approaches
- Bitcoin traders offer downside targets as BTC price risks sub-$25K dip
- From Bitcoin to Altcoins: Exploring the Different Types of Cryptocurrencies