How to backup your crypto wallet private keys
The private key and ownership are inextricably linked, so protecting them needs cautious consideration.To much better comprehend the concept of private secrets, lets explore how they work: Key generationA public key and a personal key are the 2 cryptographic keys that are produced when a cryptocurrency wallet is developed. The personal secret is kept private and known only to the owner, whereas the public key is readily available to all and acts as an address to get funds.Ownership and securityThe private key belongs to the owner alone and operates similarly to a digital signature. On Oct. 25, crypto recovery firm Unciphered used to open Stefan Thomas IronKey hard drive consisting of 7,002 BTC in an open letter, however Thomas has not reacted to the offer.How to back up personal keys Backing up personal secrets can be done through different methods, each with its own advantages and drawbacks.Paper walletsUsing paper wallets, which are concrete documents that hold an individuals public address and private key, is a typical method to back up personal keys. Because anybody who knows the mnemonic expression can access the associated personal secret and funds, its crucial to keep it personal and not disclose it to unknown parties.Step-by-step guide to recuperating a wallet utilizing backed-up private keys To safeguard your funds, there are numerous actions involved in recovering a crypto wallet using backed-up personal secrets, as explained listed below: Step 1: Gathering the required itemsYou needs to first acquire the products needed for the wallet recovery procedure. Thoroughly go into the personal key connected to your wallet (and make sure it is accurate) after picking the “Import Private Key” option.Step 4: Verifying and securingThe wallet software looks up the corresponding balance on the blockchain after the personal key is gotten in.
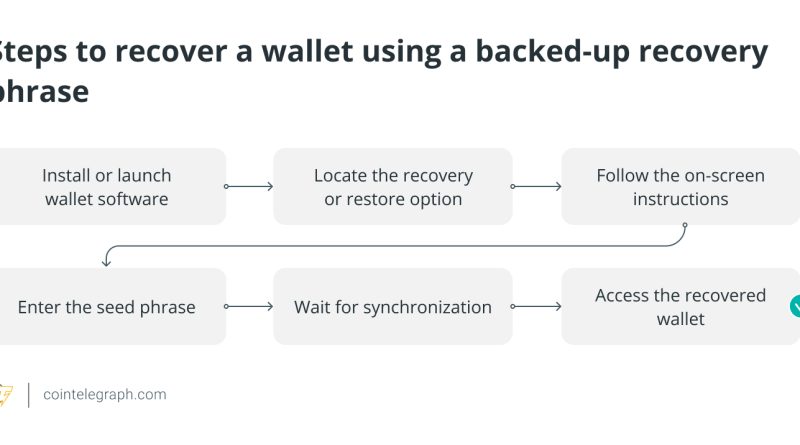
In the rapidly progressing world of cryptocurrencies, it is critical to protect ones digital possessions. A crucial element of crypto security is keeping a backup of private keys. Private keys are the secrets to ones crypto kingdom, and losing them can cause an irreversible loss of money. This post will describe the importance of personal secrets, the threats they pose and the different methods to safely backup keys.What are personal keys?In the world of cryptocurrency, every digital wallet is built on a structure of cryptographic keys, forming an important component of its structure. These keys, unique to every user, play an essential role in securing ones properties. The private key, operating comparable to a password, functions as the gateway to accessing funds, while the public crucial mirrors the wallet address, allowing seamless transactions. Generated through complex algorithms, personal secrets are the linchpin of ownership in the digital possession realm.In contrast to standard banking systems, where misplaced login qualifications are frequently recoverable, a lost private type in the cryptocurrency world can not be recuperated. For that reason, the private secret and ownership are inextricably connected, so safeguarding them needs careful consideration.To better understand the concept of private secrets, lets explore how they work: Key generationA public secret and a personal secret are the two cryptographic secrets that are generated when a cryptocurrency wallet is developed. The personal key is kept confidential and understood only to the owner, whereas the public key is readily available to all and functions as an address to receive funds.Ownership and securityThe private secret comes from the owner alone and operates likewise to a digital signature. It needs to constantly be kept secret and safe. The connected cryptocurrency funds are under the jurisdiction of anyone who has access to the private key. Private secrets can be kept by users in a range of formats, including encrypted digital files, paper wallets and hardware wallets.TransactionsA user utilizes their private key to sign deals when they wish to send cryptocurrency from their wallet. This signature is verified by the network utilizing the matching public secret. The transaction is accepted and posted to the blockchain, confirming the money transfer if the signature is legitimate.Access and controlHaving the private essential makes it possible for a specific to access and manage the funds. It is imperative that the personal secret be kept private and not disclosed to any parties. The truth that there is normally no ways to obtain the linked funds in case a private key is lost or compromised highlights how crucial it is to secure this delicate data.Risks connected with losing access to private keysIn the digital world, losing access to personal secrets may posture substantial risks, specifically when it concerns online security and cryptocurrencies. Confirming and enabling safe transactions identification need the usage of personal secrets. A user may suffer monetary loss and perhaps deal with legal problems if they lose their personal secrets, which essentially offers them no control over their digital possessions.Furthermore, internet security is jeopardized by losing personal secrets. These secrets offer a hacker the capability to impersonate the user, which might result in identity theft, unlawful access to private information or even financial fraud. It highlights how essential it is to protect private keys and employ safe backup procedures to prevent such alarming circumstances.The examples of James Howells and Stefan Thomas show the major risks related to losing access to private keys. In 2013, Howells, a British IT expert, inadvertently tossed away a hard disk drive that had his Bitcoin (BTC) private secrets. The BTC on the disk is worth countless dollars now, but its buried in a land fill and can not be accessed.Similar to this, programmer Stefan Thomas has 7,002 BTC worth tens of millions of dollars, but the funds are locked away since he forgot his password. On Oct. 25, crypto healing firm Unciphered provided to open Stefan Thomas IronKey hard disk consisting of 7,002 BTC in an open letter, but Thomas has actually not reacted to the offer.How to support private keys Backing up personal keys can be done through different techniques, each with its own advantages and drawbacks.Paper walletsUsing paper wallets, which are concrete files that hold an individuals public address and personal secret, is a common approach to back up private keys. Because it can not be hacked online, producing a paper wallet offline offers higher security. Paper wallets are prone to deterioration over time, loss or physical damage. They also make regular transactions tough due to the fact that one has to import the private secret into a digital wallet, which can be a hassle.Hardware walletsHardware wallets, which are real physical gadgets made especially for securely keeping personal secrets offline, are an extra protected choice. Hardware wallets are resistant to malware and computer infections and supply increased security. They accept a variety of cryptocurrencies and are practical to utilize. Even if they are a one-time expense, there is still a possibility of theft, loss or damage, although they are more resilient than paper wallets.Encrypted digital fileKeeping private keys on an external storage gadget, like an external tough drive or USB drive, as an encrypted digital file is another popular approach. In addition to being convenient, this technique can be secured for increased security. But theres also an opportunity of digital theft and data corruption, so regular backups and encryption are essential.Encrypted cloud storageUsing encrypted cloud storage services is another technique. Encrypted private keys can be safely kept in the cloud and accessed only with a strong passphrase. This method has the capability to be accessed from any place with a web connection and often features automated backup abilities. It raises questions about the cloud service companys security and dependability, as well as the potential for a data breach in the event that the service is compromised.Mnemonic phrasesMnemonic phrases– likewise referred to as seed or healing phrases– are employed for wallet healing functions. The healing phrase is a human-readable and user-friendly backup that, when needed, can be utilized to restore the private keys connected with a wallet.These word sequences are developed using a user and an algorithms private key. In case of a loss, mnemonic expressions can be used to recuperate the personal secret, if saved securely. This approach is helpful for people who would rather not depend upon digital or physical backups. However given that anyone who understands the mnemonic phrase can access the related private key and funds, its crucial to keep it private and not divulge it to unidentified parties.Step-by-step guide to recuperating a wallet utilizing backed-up private secrets To protect your funds, there are numerous steps involved in recovering a crypto wallet utilizing backed-up private secrets, as described listed below: Step 1: Gathering the required itemsYou needs to first get the products needed for the wallet recovery treatment. This involves downloading and having the main wallet software application ready for setup, in addition to ensuring the personal keys are safely backed up.Step 2: Installing the wallet softwareYou now need to install the wallet software application. You need to introduce the software and follow the on-screen instructions to end up the setup treatment. To lessen security threats, the wallet software application must be downloaded from the official website.Step 3: Accessing the walletOnce the software is installed, open the wallet and look for the function that permits bring back funds or importing an already-existing wallet. Thoroughly get in the personal key connected to your wallet (and ensure it is accurate) after selecting the “Import Private Key” option.Step 4: Verifying and securingThe wallet software looks up the corresponding balance on the blockchain after the private secret is entered. The shown balance needs to show your expectations, which you need to confirm. You likewise should take additional security preventative measures for the wallet, such as configuring a passcode or utilizing any other available security features.Step 5: Backing up and testingYou need to make a new backup after your wallet has actually been brought back and protected. Any modifications to passwords should be consisted of in this backup, as they are subject to updates. Recovery expressions and personal secrets, being fundamental to the wallets security, ought to stay unchanged and do not need to be upgraded in subsequent backups. Next, you need to send and receive a small quantity of cryptocurrency from the wallet to test deals and make sure the recovery is successful.Step 6: Additional security measuresHere, you need to think about extra security safety measures. This can entail creating frequent backups and, if the wallet supports it, turning on two-factor authentication. Maintaining the security of the funds requires keeping the wallet software upgraded with the newest security patches and features.How to recuperate a wallet using a backed-up healing phraseUsing a backup seed phrase to recover a wallet is an uncomplicated process that requires gaining access to the wallets healing feature. The first action for the user must be to set up or launch the wallet software application for the cryptocurrency they want to return. Upon opening the software application, the user needs to locate the wallet recovery or restore alternative, normally discovered in the settings or primary menu, and identified as “Recover Wallet” or a comparable term.After picking the healing choice, the user needs to follow the guidelines displayed on the screen. When the wallet is very first established, they will probably be asked to get in the seed phrase in the correct order. The user might need to reset the password for the retrieved wallet if the wallet software needs it.Subsequently, the user must patiently wait for the wallet software to integrate. This process makes sure that the wallet is updated with the current deals and details. Following successful synchronization, the user must have access to their recuperated wallet, complete with the proper balance and deal history.Is there a modification in the personal keys when a wallet is recovered?In most basic wallet recovery procedures, the private key connected with a particular wallet address remains the very same. The objective is to gain back access to the same wallet using the same private keys when a user recuperates a wallet using a recovery expression or any other backup method.The recovery procedure usually includes the user using the backup (such as a healing expression) to restore the initial personal secrets that were related to the wallet. If the healing achieves success, the user will have access to the same funds and addresses that remained in the wallet before any issues occurred.However, users need to comprehend the particular information and nuances of the wallet software application or service they are utilizing, as there could be variations in how various wallets deal with healing. They should follow the instructions provided by the wallet supplier to guarantee a accurate and smooth recovery process.Common errors to prevent during the wallet recovery processUsers need to work out care during the wallet recovery procedure to avoid normal issues that might result in the loss of their cryptocurrency funds. Typing the private key improperly is a serious error that might trigger access to be completely lost. Users should avoid jeopardizing their wallets security by revealing their healing expressions and/or personal keys to outside parties. Another threat is falling for phishing rip-offs; users ought to constantly confirm the URLs of sites before inputting crucial data. Lastly, there are major risks connected with not upgrading anti-viruses software and not supporting recently produced private secrets (in case funds are transferred to a brand-new secret). Likewise, malware can be presented by disregarding authorized sources and downloading software from suspicious websites.