New tech could make crypto and Web3 wallets more convenient
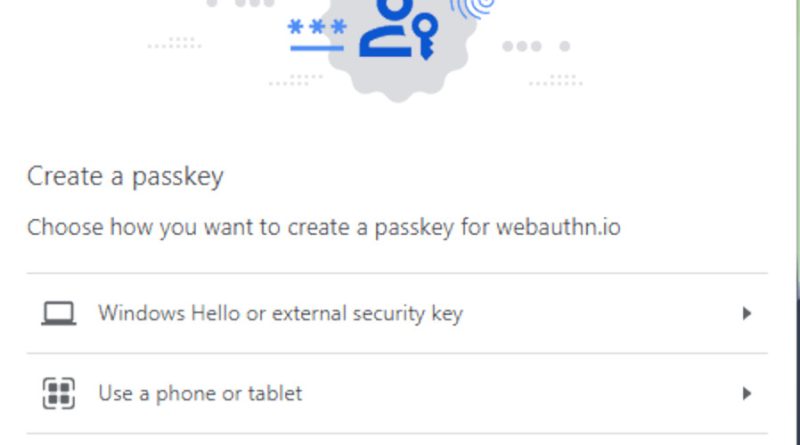
New users must discover to copy down their seed words and keep them in a safe location, create a strong password to secure their keystore file, copy addresses properly when sending funds, and other things they may never ever have to discover when utilizing a Web2 app.If a brand-new user desires to make onboarding more accessible, one choice is to use a custodial wallet provider, such as a central exchange. The world has witnessed centralized exchanges like Mt. Gox, QuadrigaX and FTX go insolvent from hacks or outright fraud, triggering some customers to lose all their funds due to utilizing a custodial wallet.Because of this danger, many crypto users still see a noncustodial wallet backed up by a set of seed words as the only safe and secure method for a user to protect their Web3 identity.But do users constantly have to pick between security and benefit? Once theyve got access to the HSM, they can license any deals from the users account.For this reason, both Immutable Passport and Kresus strategy to use two-factor authentication (2FA) as an extra layer of security in case a users e-mail account becomes compromised.Wallets based on Magic do not have passwords, so they cant be hacked through the typical method of taking and splitting a password hash.Web3AuthAnother brand-new wallet infrastructure designers are frequently utilizing is Web3Auth.Web3Auth is a crucial management network that relies on multiparty calculation (MPC) to make personal keys recoverable. If the provider declines to give the user their 2nd share after theyve properly validated, the user can generate their personal key using a combination of the share kept on their gadget plus the backup share.Related: Multiparty calculation might offer increased protection for walletsOn Web3Auth, the login supplier share is more split into 9 different fragments and distributed across a network of storage nodes, with 5 fragments being needed to rebuild the provider share. On Dfns, the nodes are configured just to sign a transaction with their fragment if the end-user has authenticated utilizing this protocol.When a user registers for a site using WebAuthn, the site develops a personal secret on the users gadget.
The foundation of the Web3 environment is the wallet, an app or internet browser extension that lets users validate their web identities and authorize deals. Using a wallet has always included a steep knowing curve. New users must find out to copy down their seed words and save them in a safe place, create a strong password to secure their keystore file, copy addresses accurately when sending funds, and other things they might never need to learn when using a Web2 app.If a new user wishes to make onboarding more available, one alternative is to use a custodial wallet company, such as a centralized exchange. But skilled crypto users will usually caution them against this for a good reason. The world has experienced centralized exchanges like Mt. Gox, QuadrigaX and FTX declare bankruptcy from hacks or straight-out fraud, triggering some clients to lose all their funds due to utilizing a custodial wallet.Because of this danger, many crypto users still see a noncustodial wallet backed up by a set of seed words as the only safe way for a user to secure their Web3 identity.But do users constantly have to pick in between security and benefit? Or is there a way to combine a noncustodial wallets security with an exchanges benefit? A few Web3 business are attempting to produce wallets that are simple to use however also dont require the user to place all their trust in a central custodian. Companies like Magic, Dfns, Kresus, Web3Auth, Immutable and others believe that a wallet can be simply as simple to utilize as an email account, and secure enough to be depended protect the users identity and funds. These companies are utilizing various types of new wallet facilities to make this idea a reality.Here is a rundown of a few of the options utilized by wallet developers: MagicOne brand-new system is the Magic software application designer set (SDK), produced by Magic Labs. It is a developer package and wallet facilities that enables developers to develop seedless wallets for users.Instead of saving the personal key on the users gadget, an encrypted copy is kept an Amazon Web Services Hardware Security Module (HSM). The encryption is performed utilizing a Master Key that can not leave the HSM. All signing is done within the HSM, preventing the users secret from being relayed to the internet.Magic wallets do not use passwords. Rather, when users initially register for a magic wallet, they send their e-mail address to the Magic relayer. The relayer then sends a one-time use token to the user through their e-mail. This token will only work if used by the gadget that sent out the demand and only for a limited time.The token is used to verify with Amazon Web Services when the user clicks a link within the e-mail. The blockchain wallet accounts personal and public keys are then produced on the users device and sent out to the HSM. Magic Labs says they can not see the created private secret, as it never goes to their servers.When users stop utilizing their wallets and close their browsers, they can reopen their wallets by repeating the process. They send their email address to Magic once again and get a new, one-time-use token. This time, after authenticating, they restore access to their wallet.Magic Labs has actually created a demonstration revealing how the system works. It appears to enable anyone to produce a wallet without downloading an internet browser extension or copying down seed words. It likewise enables users to close out their internet browsers and return to their wallets later on, logging into the very same Web3 account again.The demonstration currently just works on testnets such as Goerli, Sepolia and Mumbai.Wallets based upon MagicA few various wallets have actually been launched or are currently in advancement that use Magic. One significant example is the Kresus wallet, a mobile app that allows users to hold and store Bitcoin (BTC), Ether (ETH), Solana (SOL), Polygon (MATIC) and tokens from these networks. It also enables users to send crypto using.kresus domain names instead of crypto addresses.Kresus was released in the Apple App Store on May 11. The team informed Cointelegraph that an Android variation would come later in 2023. Immutable Passport is another example. Its an application programs user interface (API) developed by Web3 game designer Immutable. When participating games incorporate their sites with Passport, it permits players to create wallets straight through the video games site.Related: What is Immutable, explainedImmutable told Cointelegraph that Passport wallets link to the Immutable X network, a layer-2 Ethereum procedure, which permits players to keep all of their Immutable video gaming antiques in one account, despite which video game they at first registered with.Immutable recently executed Passport as the default login technique for its developer website, and they prepare to utilize it for a minimum of one video games login page by summer season 2023, the team said.Security concerns with MagicThe Magic SDK does consist of one known security defect, which developers have actually taken actions to reduce. Since it counts on email tokens to authenticate a user, an assailant can potentially get access to a users HSM by hacking into their e-mail account and after that asking for to authenticate from the assaulters own gadget. Once theyve got access to the HSM, they can authorize any transactions from the users account.For this reason, both Immutable Passport and Kresus strategy to utilize two-factor authentication (2FA) as an additional layer of security in case a users e-mail account ends up being compromised.Wallets based on Magic do not have passwords, so they cant be hacked through the typical approach of stealing and splitting a password hash.Web3AuthAnother new wallet facilities designers are often using is Web3Auth.Web3Auth is a crucial management network that depends on multiparty computation (MPC) to make private keys recoverable. When users sign up for an account utilizing Web3Auth, they generate a personal key as normal. This key is split into three “shares.” The first share is kept on their gadget, the 2nd is stored by the Web3Auth network through a login company, and the 3rd is a backup share that must be stored on a separate device or offline. The third share can likewise be generated from security concerns if the user prefers.Because of the way multiparty calculation works, a user can create the private secret and confirm transactions with only two of the 3 shares. This suggests the user can still recuperate their wallet if their gadget crashes or they lose their backup secret. At the very same time, the login provider can not carry out deals without the users permission considering that the provider only has one share. The provider also can not censor transactions. If the supplier refuses to offer the user their 2nd share after theyve properly validated, the user can produce their private secret utilizing a combination of the share kept on their device plus the backup share.Related: Multiparty computation could provide increased defense for walletsOn Web3Auth, the login service provider share is further split into 9 various fragments and dispersed throughout a network of storage nodes, with five shards being required to reconstruct the supplier share. This prevents the login provider from keeping its shares by itself infrastructure.Web3Auth walletsWeb3Auth has actually been incorporated into a number of retail wallets, including Binance Wallet and a closed beta version of Trust Wallet. In the extension variation of Binance Wallet, users can create wallet accounts using their Google logins. In the Trust Wallet version, Google, Apple, Discord and Telegram are login supplier choices, according to a main video from Web3Auths Twitter account.In either case, the user still needs to copy down seed words. However, the account can be recuperated even if these words are lost, so long as the user still has access to both their device and login service provider account.Speaking to Cointelegraph, Web3Auth CEO Zhen Yu Yong argued that the shift to utilizing numerous crucial shares in Web3 resembles the development of 2FA on Web2 websites, specifying:”Usernames and passwords in the early 2000s or late 1990s were extremely simple to lose. Back then, we believed that financial applications would never be built on the web.””With usernames and passwords, we eventually advanced into two-factor authentication,” Yong continued. “I think thats the very same shift were attempting to push here […] Instead of utilizing a single factor seed phrase, were splitting this up into multiple different elements […] and doing it such that its all your access points, so its all still self-custodial.”DfnsDfns, pronounced as “defense,” is an MPC crucial management network that allows end-users, institutions and developers to create passwordless and seedless wallets. It holds each blockchains personal secret as numerous shards spread among nodes throughout the Dfns network. To authorize a deal, the Dfns nodes need to collectively produce a signature utilizing each shard.Unlike Web3Auth, Dfns does not keep a share of the blockchain private key on the users device or as a backup. All of the fragments are continued the network itself.The Dfns nodes use a protocol called “WebAuthn” to verify that a user has actually authorized a deal. This procedure was produced by the World Wide Web Consortium to permit users to log into sites without a password. On Dfns, the nodes are configured only to sign a deal with their fragment if the end-user has actually authenticated utilizing this protocol.When a user signs up for a site utilizing WebAuthn, the website creates a personal key on the users device. This private secret is not used in any blockchain. It just exists to enable the user to log in to the site. When the secret is created, the user is triggered to safeguard the key with a pin code or biometric lock. On a Windows PC, this lock can be produced through Windows Hello, which is part of the operating system, or through a separate gadget such as a cellphone or Yubikey. On a mobile device, the lock is produced using the devices built-in security.Example of a WebAuthn registration prompt. Source: WebAuthn.ioOn a site that executes WebAuthn registration, the user does not need an e-mail address or password to sign up. Instead, the gadget utilizes its own security system to determine the user.Related: Gemini unveils Yubikey integrationWhen a wallet development group produces a wallet utilizing Dfns, they can give this authentication method to the end-user. In this case, the wallet is thought about noncustodial due to the fact that the wallet company does not have the users device, pin code or biometric information and for that reason cant authorize transactions.The end-user can likewise include gadgets to a wallet if the first one crashes.Wallet developers can develop custodial wallets utilizing Dfns. In this case, the wallet designer needs to validate with the network utilizing WebAuthn. They can utilize any technique to verify a user with themselves, consisting of even usernames and passwords.Wallets that use DfnsSpeaking to Cointelegraph, Dfns founder Clarisse Hagège mentioned that a lot of the platforms clients are organizations and development groups in the business-to-business market. The group has started to draw in more business-to-consumer wallet companies just recently. The retail crypto savings app SavingBlocks uses Dfns, and the business remains in talks with a couple of decentralized exchanges to assist produce wallets for their consumers as well, she said.Hagège argued that for crypto mass adoption to occur, users shouldnt even understand that there is a blockchain private key when they make deals.”What were targeting is the hundreds of thousands of developers that will build use cases targeted to blockchain mass adoption, targeted to people that do not wish to know that they have a private key,” she described. “We have a network of servers that runs that key generation […], and whats crucial is not in fact owning the crucial share or the private key, however its owning the access to the API.”Will brand-new wallet tech be embraced by the masses?Whether these brand-new wallet technologies will result in mass adoption or even be accepted by present users remains to be seen. In spite of their simplicity, they may still be too complex for users that choose to hold their crypto in an exchange. On the other hand, users who think in the “not your secrets, not your crypto” mantra might be suspicious of relying on an MPC network or hardware security module owned by Amazon to authorize transactions for them.Still, some users may choose that the advantages of MPC or magic links are simply too excellent to pass up. Only time will tell.In the meantime, these new innovations will likely provoke discussion about how to guarantee users remain in control of their funds or what “self-custody” actually suggests.
Related Content
- Bitget and crypto influencer embroiled in legal saga after Reel Star token listing fiasco
- Yield Curves, Inversion, The Eurodollar And Bitcoin
- Hong Kong to list ‘suspicious’ crypto platforms in wake of JPEX scandal
- Price analysis 11/22: BTC, ETH, BNB, XRP, SOL, ADA, DOGE, TON, LINK, AVAX
- The Ultimate Guide to bitcoin regulation in 2025: 10 Effective Strategies