Only 6 out of 45 crypto wallet brands have undergone penetration testing: Report
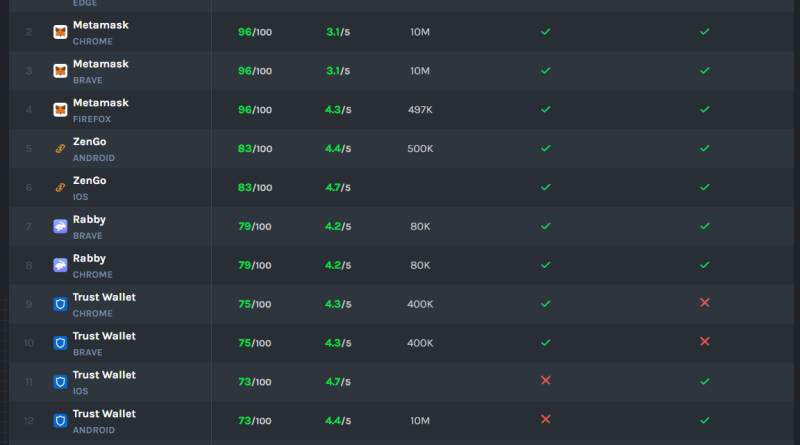
All other brands listed did not provide any evidence of having actually done these tests.The report also offered a general ranking of the security of each wallet, listing MetaMask, ZenGo, Rabby, Trust Wallet, and Coinbase wallet as being the most protected wallets overall.CER rankings for wallet security.”They found that the most popular wallet brand names were more most likely to perform security audits, consisting of penetration tests, as they often had the funds to do so:”Essentially, popular wallets tend to adopt more robust security procedures to secure their increasing user base.”CERs ranking of wallets was based on a method that consisted of factors like bug bounties, past incidents, and security features, such as bring back approaches and password requirements.Although most wallet brand names dont perform penetration testing, CER stated that many of them do rely on bug bounties to discover vulnerabilities, which is typically an efficient methods of avoiding hacks.
Thank you for reading this post, don't forget to subscribe!
All other brand names noted did not offer any evidence of having actually done these tests.The report also provided an overall ranking of the security of each wallet, noting MetaMask, ZenGo, Rabby, Trust Wallet, and Coinbase wallet as being the most secure wallets overall.CER rankings for wallet security.”They discovered that the most popular wallet brand names were more likely to carry out security audits, consisting of penetration tests, as they frequently had the funds to do so:”Essentially, popular wallets tend to embrace more robust security procedures to safeguard their increasing user base.”CERs ranking of wallets was based on a methodology that included factors like bug bounties, previous events, and security features, such as bring back approaches and password requirements.Although most wallet brands dont perform penetration testing, CER specified that numerous of them do rely on bug bounties to discover vulnerabilities, which is frequently a reliable means of preventing hacks.