What are open-source protocols, and how do they work?
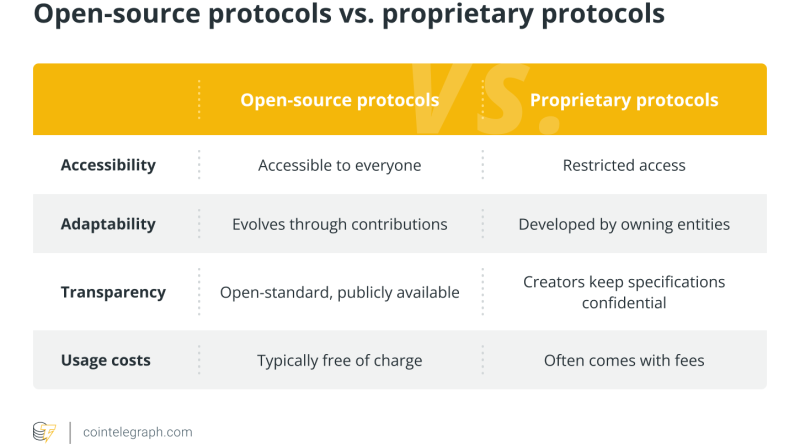
Comprehending open-source protocols Open-source procedures have become an essential in the tech world and are acquiring traction due to the myriad advantages that they provide over their exclusive counterparts.The procedures are typically created with the intent of being used by the public, making it possible for anyone to examine, change and share their code. The benefits of open-source procedures are complex, ranging from their inherent openness to their larger ease of access. Additionally, they depend on peer examinations, an inclusive and affordable model that distinguishes them from their exclusive equivalents. Popular examples of open-source software application consist of widely utilized operating systems such as Linux and Android and the popular Firefox web internet browser. When it concerns open-source cryptographic procedures, the Bitcoin, Ethereum, Cardano and Polkadot networks stand out as notable blockchain protocol exemplars, among others.Open-source vs. exclusive protocolsOpen-source and proprietary procedures represent 2 unique techniques to procedure development, each with its own set of principles when it comes to procedure implementation. The following is a dissection of their key variations: Whats the development process for open-source procedures? The development of open-source protocols involves a number of distinct phases, each important to a procedures development. Everything starts with the concept phase, where designers lay the structure that defines the protocols standards and purpose.Usually, the standard idea is based on an existing protocol with some improvements. The concept stage acts as the bedrock, upon which developers meticulously describe the architecture and features, forming a robust theoretical foundation. In this stage, designers chart out a distinct roadmap, similar to a strategic strategy, assisting the jobs trajectory.The subsequent step in the advancement process is usually the prototyping stage. In this phase, developers create a functional design of the protocol that consists of the essential proposed functions. The prototype is generally made accessible to the general public as the beta version.Releasing the beta variation topics the software to real-world scenarios and user interactions, allowing developers to recognize its weaknesses and strengths. The stage likewise permits designers to get feedback from the open-source neighborhood regarding prospective brand-new features to incorporate before the last protocol is released. For that reason, the phase is appropriately described as the beta screening or user acceptance screening (UAT) stage.Continuous feedback and updating guarantee that the procedure stays responsive to the progressing requirements and expectations of its user base. After appropriate protocol upgrades are carried out to deal with a number of the known stability and reliability problems, the protocol reaches a level of stability calling for the classification of a “stable release.” The stable release version is generally as reliable as designers can make it.However, the procedure does not culminate in steady releases. Open-source jobs need continuous protocol maintenance. The procedure usually involves releasing bug fixes, such as security spots, and updating the code for enhanced compatibility. Are open-source protocols copyrighted? When a developer releases their code as open-source, they are sharing it with the public, allowing others to utilize, modify and disperse it. However, the act of making the code public doesnt equate to unrestricted usage.Copyright laws apply here, just as they do for exclusive software. The laws automatically secure any initial creative work, consisting of open-source procedures, granting the software application developer unique rights to control their usage and distribution.When it pertains to open-source procedure licensing, the developer generally connects a license to it, which functions as a set of guidelines that plainly defines whats permissible and whats off-limits concerning the code.Open-source licenses often approve users substantial approvals without needing specific approval from the original author. That said, there are 2 main kinds of open-source licenses: liberal and copyleft. A permissive license, in some cases likewise called a BSD-style or Apache-style license, imposes minimal requirements on how the software application can be customized or rearranged. Projects that utilize this type of license are required to add a service warranty disclaimer. A timeless example of a liberal license is the MIT License. The license permits anybody to use, distribute the code and modify without prior consent.Projects using MIT-licensed code typically must include the original copyright notice and a disclaimer explicitly stating that the software comes with no warranty. The disclaimer clarifies that the copyright holders bear no duty for any claims or liabilities coming from the software applications use.The license is extremely liberal and is crafted to use optimum freedom to designers, even allowing the codes inclusion and distribution in industrial products.Regarding copyleft licenses, jobs that utilize them are likewise required to attach a liability disclaimer. They include more restrictions, especially worrying the circulation of customized procedure variations. For circumstances, the copyleft GNU General Public License (GPL), a widely utilized open-source license, assurances that the software application remains open and totally free. Like the MIT License, the GPL mandates a service warranty disclaimer.Copyleft licenses guarantee that open-source protocols or software can be used, fine-tuned and shared without constraints. Any customized work must adhere to the very same terms, maintaining the protocols openness in all future versions.When it comes to exclusive protocols, the landscape changes considerably. The procedures enforce rigid restrictions on their protocol documents, which frequently consist of constraints on modifying or reverse-engineering the code.To promote procedure security, exclusive tasks normally consist of confidentiality clauses in their licenses, avoiding users from divulging their protocols workings or any proprietary info they may come across.In regards to expense, copyleft and permissive licenses are totally free, allowing users to utilize and disperse the software application without charge. On the other hand, exclusive licenses often need users to spend for access to and usage of the software. The future of open-source protocols As the world ends up being interconnected and significantly digital, open-source protocols are poised to play an essential function in allowing development, specifically when it comes to supporting interoperability among various systems, applications and devices.The shift is driven by the extensive, concurrent utilization of protocols crafted by various developers on a daily basis. As an outcome, open-source procedures, particularly those that enable modifications by third celebrations and support interoperable systems, are bound to take spotlight in the brand-new technological frontier.Going by present patterns, open-source projects are likewise most likely to concentrate on sustainability, energy performance and problem-solving in alignment with the international push for environment-friendly technological solutions.Furthermore, open-source networking protocol initiatives are anticipated to continue developing peer-to-peer (P2P) internet procedures. The procedures assist in direct interaction in between systems, removing the requirement for central intermediary systems. P2P procedures boast a broadening range of applications, particularly in allowing P2P transactions and communications through decentralized protocols.
Understanding open-source procedures Open-source procedures have ended up being an essential in the tech world and are gaining traction due to the myriad benefits that they offer over their proprietary counterparts.The procedures are normally produced with the intent of being utilized by the public, making it possible for anyone to analyze, modify and share their code. The laws instantly safeguard any original imaginative work, including open-source procedures, approving the software application developer exclusive rights to manage their use and distribution.When it comes to open-source procedure licensing, the designer generally connects a license to it, which acts as a set of guidelines that plainly defines whats allowable and whats off-limits worrying the code.Open-source licenses often grant users extensive consents without requiring specific approval from the initial author. The protocols impose stringent limitations on their procedure documentation, which typically include limitations on modifying or reverse-engineering the code.To support procedure security, exclusive jobs usually include privacy provisions in their licenses, avoiding users from disclosing their protocols workings or any proprietary details they might come across.In terms of expense, permissive and copyleft licenses are totally free, allowing users to disperse the software application and use without charge. The future of open-source procedures As the world ends up being increasingly digital and interconnected, open-source protocols are poised to play an essential function in making it possible for development, particularly when it comes to supporting interoperability amongst various systems, applications and devices.The shift is driven by the widespread, concurrent usage of procedures crafted by various developers on a daily basis. As an outcome, open-source procedures, specifically those that enable changes by third parties and assistance interoperable systems, are bound to take center phase in the new technological frontier.Going by existing patterns, open-source projects are likewise most likely to focus on sustainability, energy efficiency and problem-solving in positioning with the international push for eco-friendly technological solutions.Furthermore, open-source networking procedure initiatives are expected to continue developing peer-to-peer (P2P) web protocols.
Related Content
- Germany’s blockchain funding increases 3% amid market downturn: Report
- NFT gas usage shows downward trend, signals shift in landscape
- Nifty News: Metaverse bank robberies, Trump NFT biz prefers crypto over cash, and more
- Twitter Community Notes hits 44 countries as Elon Musk seeks ‘truth’ for X
- Bitcoin forgets Fed as trader eyes classic BTC price ‘liquidity hunt’