Windows tool targeted by hackers deploys crypto mining malware
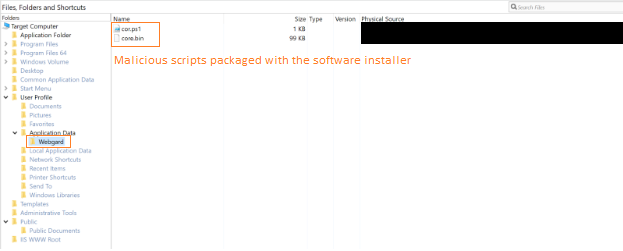
Hackers have actually been utilizing a Windows tool to drop cryptocurrency-mining malware given that November 2021, according to an analysis from Ciscos Talos Intelligence. The attacker makes use of Windows Advanced Installer– an application that assists designers plan other software application installers, such as Adobe Illustrator– to carry out destructive scripts on contaminated makers. According to a Sept. 7 post, the software installers impacted by the attack are mainly utilized for 3D modeling and graphic style. Furthermore, most of the software installers utilized in the malware project are written in French. The findings recommend that the “victims are likely across company verticals, including architecture, engineering, building and construction, manufacturing, and entertainment in French language-dominant countries,” explains the analysis. The attacks primarily impact users in France and Switzerland, with a few infections in other nations, including the United States, Canada, Algeria, Sweden, Germany, Tunisia, Madagascar, Singapore and Vietnam, the post keeps in mind based upon DNS request information sent to the attackers command and control (C2) host. The illegal crypto mining campaign determined by Talos involves the release of malicious PowerShell and Windows batch scripts to perform commands and develop a backdoor in the victims maker. PowerShell, particularly, is well-known for running in the memory of the system instead of the disk drive, making it more difficult to determine an attack. Example of a software installer packaged with harmful scripts utilizing Advanced Installer. Source: Talos Intelligence.Once the backdoor is set up, the assaulter carries out additional hazards, such as the Ethereum crypto-mining program PhoenixMiner, and lolMiner, a multi-coin mining threat.”These destructive scripts are executed utilizing Advanced Installers Custom Action function, which allows users to predefine customized setup tasks. The final payloads are PhoenixMiner and lolMiner, publicly readily available miners relying on computer systems GPU capabilities”The usage of crypto mining malware is understood as cryptojacking, and includes installing a crypto mining code on a device without the users understanding or authorization in order to unlawfully mine cryptocurrencies. Indications that mining malware might be running in a device consist of getting too hot and improperly performing devices.Using malware households to hijack devices to mine or steal cryptocurrencies isnt a brand-new practice. Previous smart device giant BlackBerry just recently recognized malware scripts actively targeting at least 3 sectors, consisting of monetary services, health care and government.Magazine: Moral duty– Can blockchain really improve trust in AI?
Related Content
- BTC price gets $36K FOMC target as Bitcoin prints 29% ‘Uptober’ gains
- Valkyrie ‘BRRR’ spot Bitcoin ETF enters SEC’s Nasdaq rulemaking list
- SEC calls ETF filings inadequate, Binance loses euro partner and other news: Hodler’s Digest, June 25 – July 1
- Bitcoin Plunges To Lowest Level Since January 2021
- Price analysis 8/28: SPX, DXY, BTC, ETH, BNB, XRP, ADA, DOGE, SOL, DOT