Balancer blames ‘social engineering attack’ on DNS provider for website hijack
The team behind Balancer, an Ethereum-based automatic market maker, believes a social engineering attack on its DNS service provider was what led to its websites front end being jeopardized on Sept. 19, leading to an approximated $238,000 in crypto stolen. Around 8 hours after the first caution of the attack, Balancer said its decentralized autonomous organization (DAO) was actively addressing the DNS attack and was working to recuperate the Balancer UI. At 5:45 pm UTC on Sept. 20, Balancer stated it was effective in protecting the domain and bringing it back under the control of Balancer DAO.
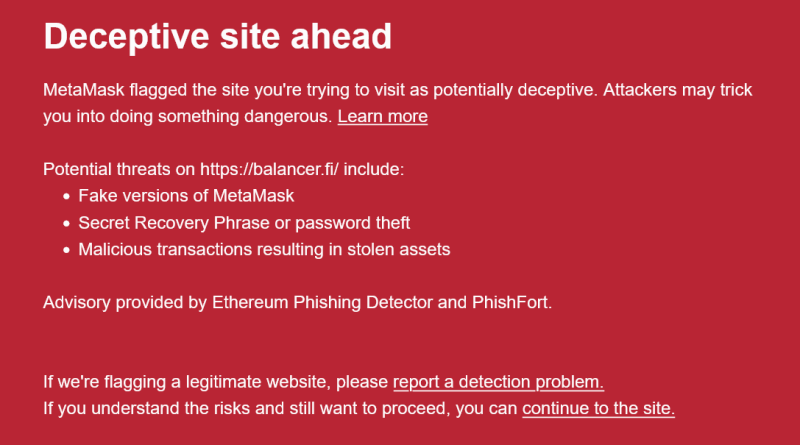
Around 8 hours after the very first warning of the attack, Balancer stated its decentralized self-governing company (DAO) was actively attending to the DNS attack and was working to recover the Balancer UI. At 5:45 pm UTC on Sept. 20, Balancer stated it was successful in securing the domain and bringing it back under the control of Balancer DAO. Regardless of Balancer confirming its subdomains on “balancer.fi” to now be safe, the “Deceptive site ahead” warning still appears when attempting to gain access to Balancers site.
In spite of Balancer validating its subdomains on “balancer.fi” to now be safe, the “Deceptive website ahead” alerting still appears when trying to gain access to Balancers website. Balancers site as of Sept. 20 at 10:22 pm UTC. Source: Balancer.Cointelegraph connected to Balancer to confirm the amount of funds lost, but did not get an immediate response.Magazine: $3.4 B of Bitcoin in a popcorn tin: The Silk Road hackers story
EuroDNS is a Luxembourg-based domain name registrar and DNS service supplier. Angel Drainer involvedBlockchain security firms SlowMist and CertiK reported that the opponent used Angel Drainer phishing contracts.SlowMist stated the exploiters assaulted Balancers site via Border Gateway Protocol hijacking– a procedure where hackers take control of IP addresses by damaging web routing tables.The hackers then caused users to “approve” and move funds by means of the “transferFrom” function to the Balancer exploiter, it explained.Related: Breaking: All funds are at threat– Steadefi made use of in continuous attackThe hacker, whom SlowMist thinks might be related to Russia, has actually currently bridged some of the stolen Ether (ETH) to Bitcoin (BTC) addresses by means of THORChain prior to ultimately bridging the ETH back to Ethereum, blockchain security firm SlowMist discussed on Sept. 20. In other words, after the aggressor (AngelDrainer) assaulted the site through BGP hijacking, then induced users to … https://t.co/5g6P2aPEz8 pic.twitter.com/3PInfe9VC1— MistTrack (@MistTrack_io) September 20, 2023
Related Content
- ‘This is the trigger’ — Arthur Hayes says it’s time to bet on Bitcoin
- 6 Questions for Kei Oda: From Goldman Sachs to cryptocurrency
- ‘One of the greatest’ Bitcoin metrics says BTC price bull run is here
- Elizabeth Warren, Bernie Sanders urge closure of ‘$50 billion crypto tax gap’
- Crypto and AI: Control the robots, incentivize the humans