Crypto firms beware: Lazarus’ new malware can now bypass detection
North Korean hacking cumulative Lazarus Group has been using a brand-new type of “advanced” malware as part of its phony employment frauds– which researchers warn is far more difficult to find than its predecessor.According to a Sept. 29 post from ESETs senior malware researcher Peter Kálnai, while examining a recent fake job attack against a Spain-based aerospace firm, ESET scientists found a publicly undocumented backdoor called LightlessCan. #ESET scientists unveiled their findings about an attack by the North Korea-linked #APT group #Lazarus that took objective at an aerospace company in Spain.
North Korean hacking collective Lazarus Group has been using a new type of “sophisticated” malware as part of its fake employment rip-offs– which researchers alert is far more tough to spot than its predecessor.According to a Sept. 29 post from ESETs senior malware researcher Peter Kálnai, while examining a recent phony job attack versus a Spain-based aerospace company, ESET researchers found a publicly undocumented backdoor named LightlessCan. #ESET scientists unveiled their findings about an attack by the North Korea-linked #APT group #Lazarus that took goal at an aerospace business in Spain. The new payload likewise uses what the scientist calls “execution guardrails”– guaranteeing that the payload can just be decrypted on the designated victims machine, consequently preventing unintentional decryption by security researchers.
The Lazarus Groups fake job rip-off typically includes fooling victims with a possible offer of work at a widely known company. The attackers would lure victims to download a malicious payload masqueraded as files to do all sorts of damage. Kálnai says the brand-new LightlessCan payload is a “considerable development” compared to its predecessor BlindingCan.” LightlessCan mimics the performances of a vast array of native Windows commands, allowing discreet execution within the RAT itself instead of noisy console executions.”” This approach offers a considerable advantage in regards to stealthiness, both in evading real-time tracking services like EDRs, and postmortem digital forensic tools,” he said. ♂ Beware of phony LinkedIn recruiters! Discover how Lazarus group made use of a Spanish aerospace company through trojanized coding difficulty. Dive into the details of their cyberespionage campaign in our newest #WeLiveSecurity post. #ESET #ProgressProtected– ESET (@ESET) September 29, 2023
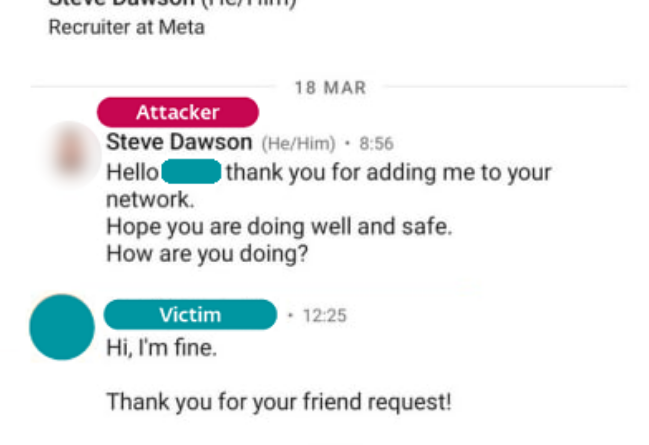
The brand-new payload likewise uses what the scientist calls “execution guardrails”– ensuring that the payload can just be decrypted on the intended victims device, consequently preventing unexpected decryption by security scientists. Kálnai said that a person case that included the new malware originated from an attack on a Spanish aerospace company when a staff member received a message from a fake Meta employer named Steve Dawson in 2022. Not long after, the hackers sent over the 2 easy coding obstacles embedded with the malware. The initial contact by the assailant impersonating an employer from Meta. Source: WeLiveSecurity.Cyberespionage was the main motivation behind Lazarus Groups attack on the Spain-based aerospace firm, he added.Related: 3 actions crypto investors can take to prevent hacks by the Lazarus GroupSince 2016, North Korean hackers have taken an approximated $3.5 billion from cryptocurrency jobs, according to a Sept. 14 report by blockchain forensics firm Chainalysis.In September 2022, cybersecurity firm SentinelOne cautioned of a fake task scam on LinkedIn, using potential victims a task at Crypto.com as part of a project called “Operation Dream Job.” On the other hand, the United Nations has beetrying to curtail North Koreas cybercrime strategies at the international level– as it is understood North Korea is utilizing the stolen funds to support its nuclear rocket program.Magazine: $3.4 B of Bitcoin in a popcorn tin: The Silk Road hackers story
Related Content
- MAYC ripoff creator pleads guilty, G2A opens NFT platform: Nifty Newsletter
- The Rise of Bitcoin: How it Became a Global Phenomenon and Why You Should Care
- The Rise of Digital Coins: What You Need to Know About Cryptocurrency
- Why is the crypto market down this week?
- Binance was wrong to boot Monero, ZCash and other privacy coins